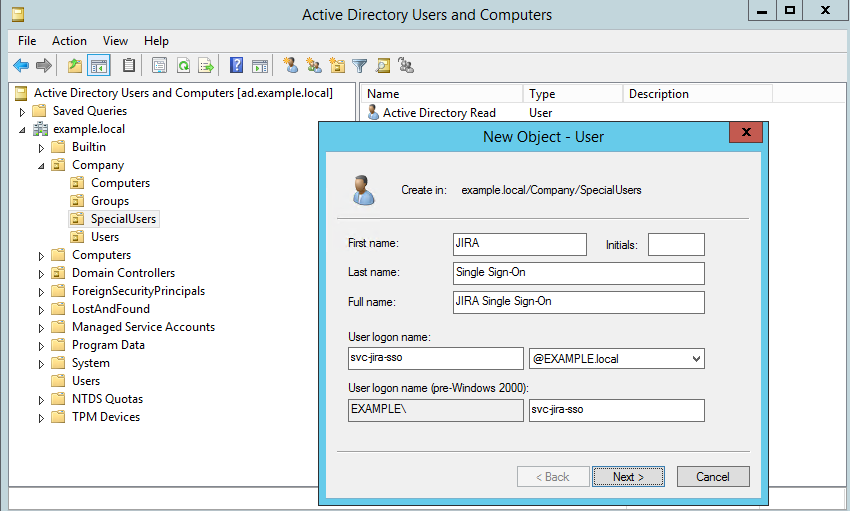
First, start off with a new user object. We recommend using a dedicated user for the purpose of mapping an SPN.
When running the ktpass-command we need a user account to hold the SPN.
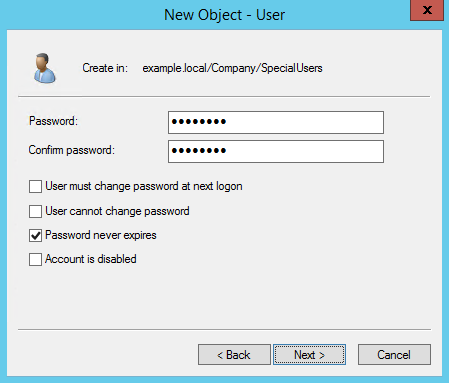
Make sure that password never expires and user cannot change password are set.
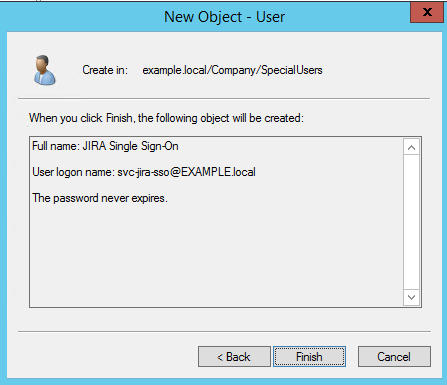
The details of the new user account.
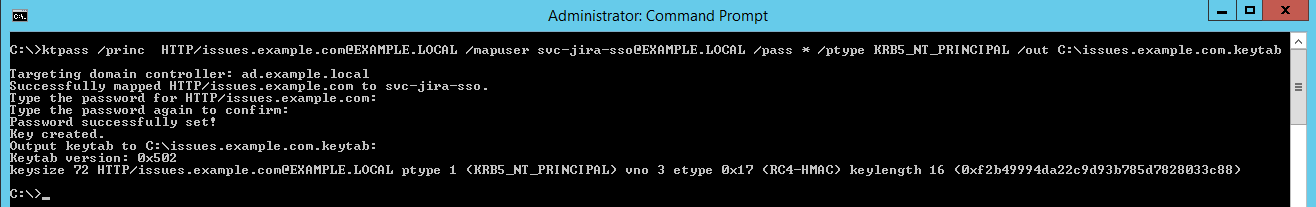
Creating the keytab with ktpass
Command / parameter |
|
|---|---|
ktpass | ktpass is included in widows 2008 onward and is located in C:\Windows\System32\ |
/princ HTTP/issues.example.com@EXAMPLE.LOCAL | HTTP - defines the protocol. HTTP (uppercase) is used regardless of accessing the site with https |
/mapuser EXAMPLE\svc-jira-sso | Maps the Service Principal name to an Active Directory user account. A unique account for each service should be created. The account should be configured with "Password never expires" and "User cannot change password" checked. |
/pass * | Some password. The password set, replaces the user password. |
/out C:\issues.example.com.keytab | The output location of the newly created keytab |
/ptype KRB5_NT_PRINCIPAL | The general ptype. Recommended by Microsoft. |
Example command:
ktpass /princ HTTP/issues.example.com@EXAMPLE.LOCAL -mapuser EXAMPLE\svc-jira-sso -pass * /out C:\issues.example.com.keytab /ptype KRB5_NT_PRINCIPAL
ktpass must be run in an elevated command prompt as a user with domain or enterprise permissions.