...
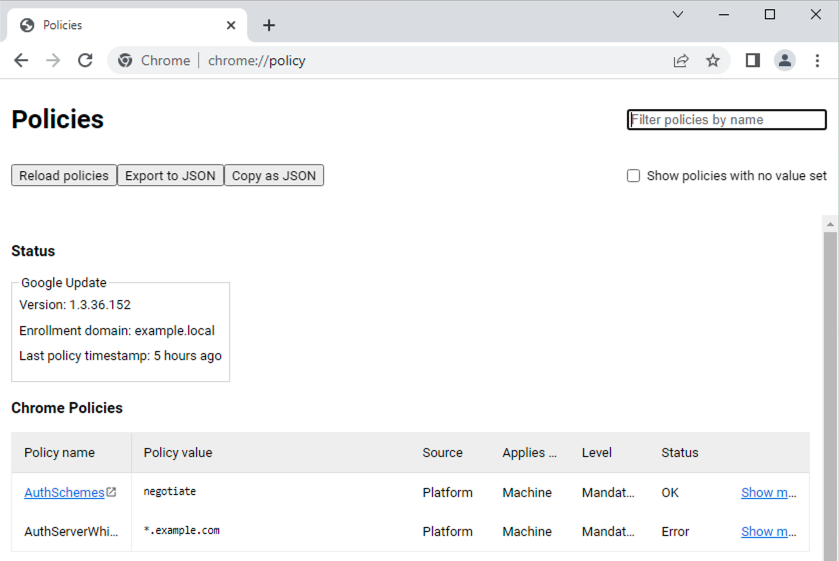
To check whether your Chrome uses the AuthServerAllowlist, take a look at URL: chrome://policy
If Chrome policies state " No policies set, " Chrome on Windows will instead use Local Intranet Zone. Your site must be added to that list for Chrome to work with Kerberos on Windows. Chrome on other operating systems requires policies to work with Kerberos.
| Info |
|---|
When defined, Chrome policies override the Windows Local Intranet Zone List. |
| Expand | ||
|---|---|---|
| ||
On OS X you may run commands below with your domain names in a terminal window to configure Chrome. Restart Chrome afterward. The first command removes the deprecated name Policies that may affect how Chrome and Kerberos works:
|
| Expand | ||
|---|---|---|
| ||
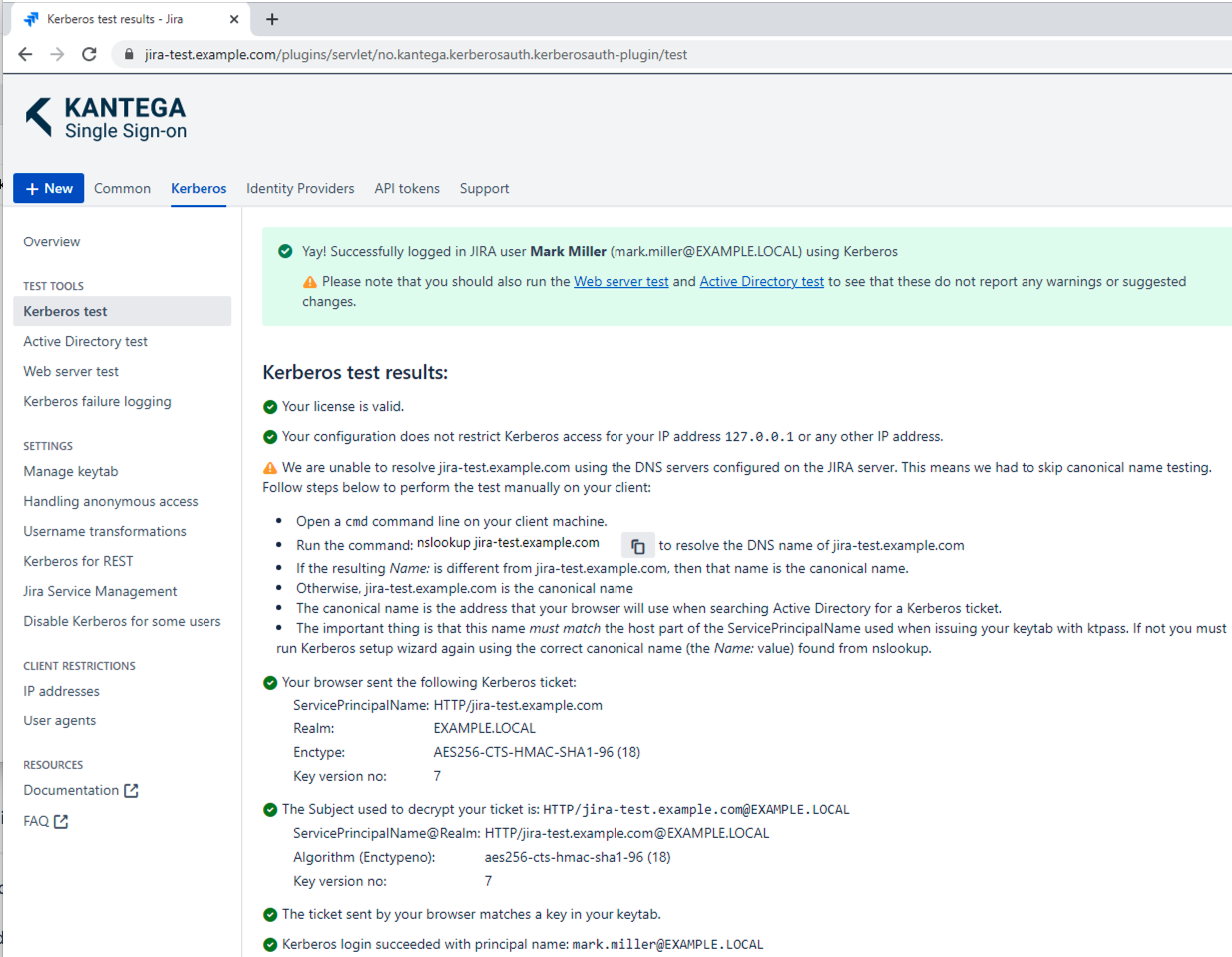
When you believe you have configured the correct group policy to have Kerberos working and also have followed guide to set up Kerberos support in Kantega SSO, please navigate to Kerberos test page verify all is set up correctly. You will on the Kerberos test page get help on what may be remaining to have your setup work: |
Using short-form URLs
| Info |
|---|
Note that when accessing the application using the short format URL (http://issues), browsers will still look for an SPN in the FQDN format (issues.example.com) |
...