These settings apply to SAML, OpenID Connect, and Windows Integrated Authentication (Kerberos) and are found under the “Common” menu.
Prevent traditional login
Kantega Single Sign-on does not prevent the usage of traditional username/password login by default. Any user can cancel SSO and log in manually, provided they are provisioned in a way that gives them passwords in the first place. This can sometimes be undesirable, for example, when users are provisioned through AD/LDAP where passwords are available - but the organization wishes to require the use of 2FA or SmartCard.
...
Note that only the standard login forms are prevented from username/password login, not the core password/directory system. Username and password login may still be usable through third-party plugins/applications if they run their own password validation.
Force login
Kantega Single Sign-on will, by default, only authenticate users where your Atlassian product would otherwise require them to log in with a username and password.
...
You may also exclude certain of the build-in path prefixes from the above list. Exclusion paths will be evaluated as "starts with". so using * in the end is not neccesary.
...
Multi-factor authentication (MFA)
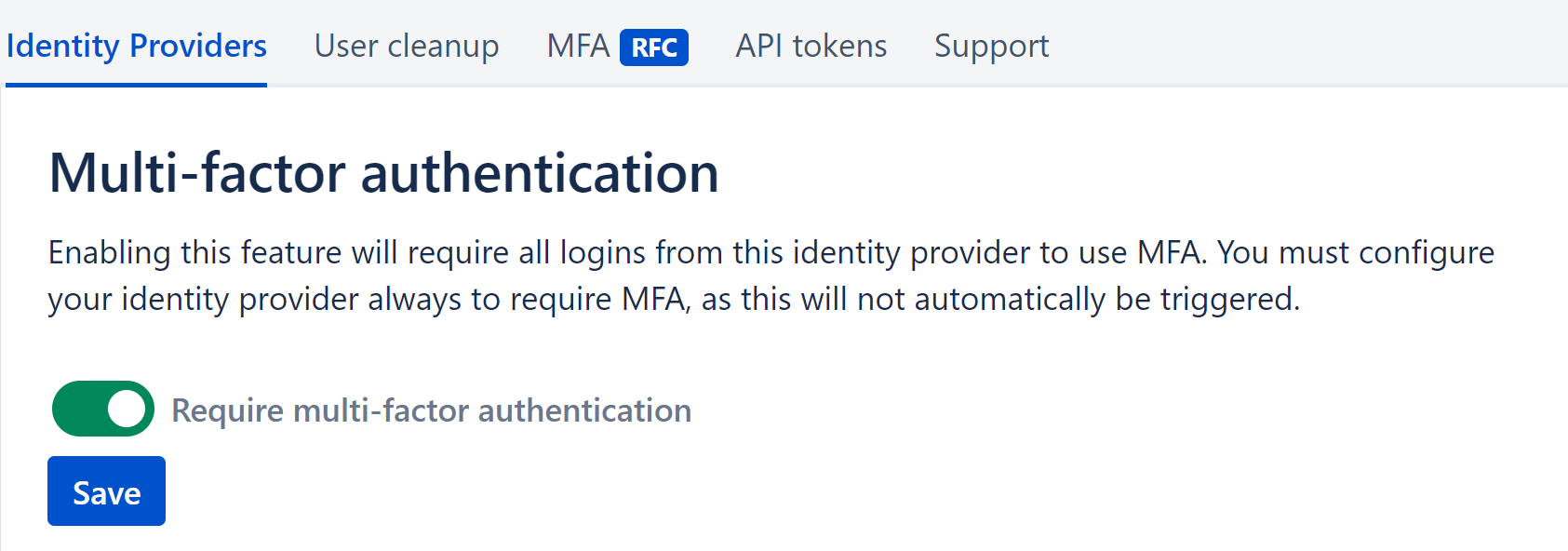
Enable multi-factor authentication requirement on your Identity provider (IDPIdP) if you require all logins from the IDP to use MFA.
...
This assures that MFA was used on the IdP side during login.
Enforce multi-factor authentication
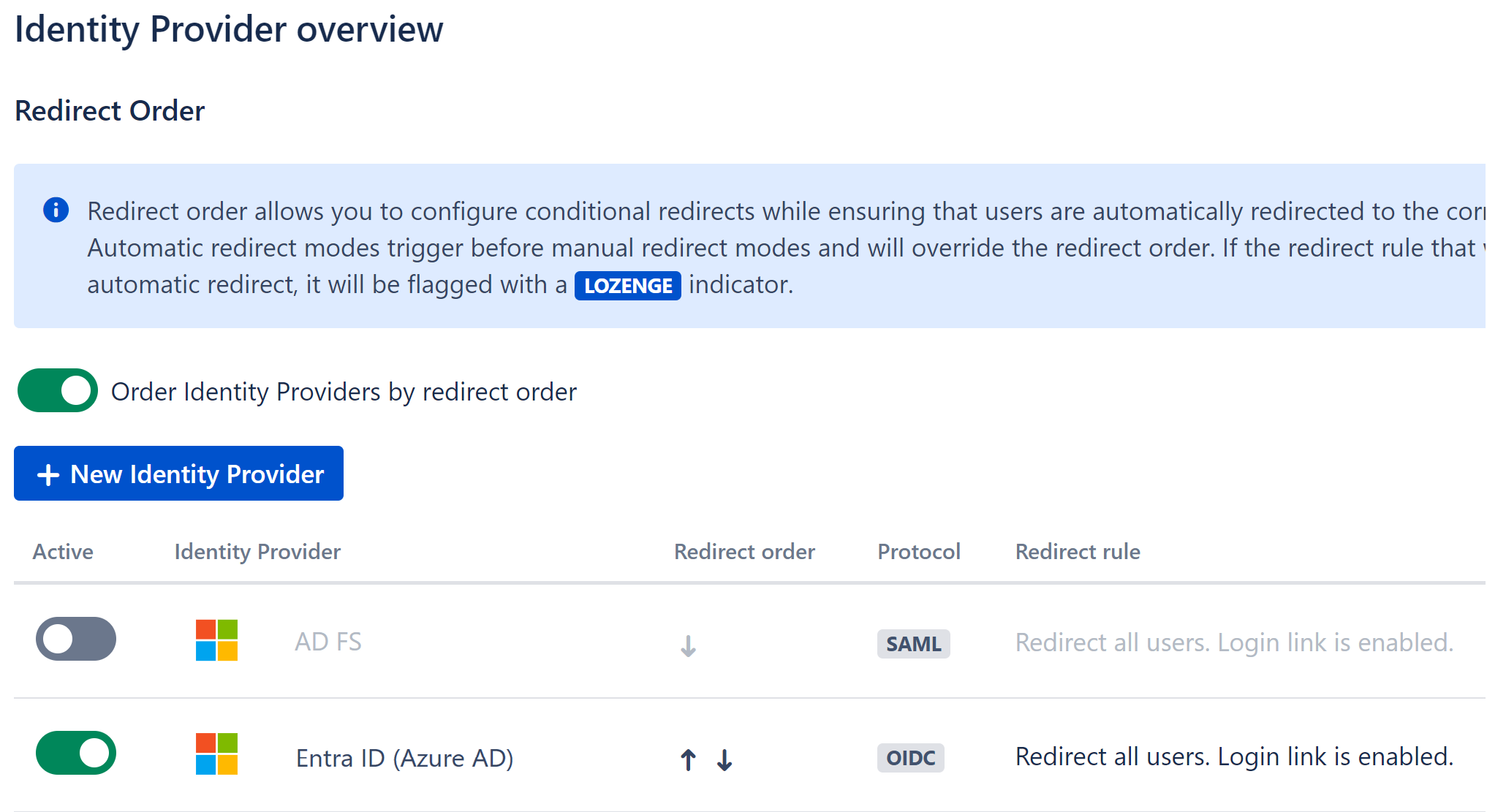
Select Identity Providers in the Ksso menu, and the identity Provider overview appears.
Select the IDP which requires MFA, and the Identity Provider settings menu appears.
Select Enforce multi-factor authentication and enable set the toggle “Require multi-factor authentication” ON.
| Info |
|---|
You must enable multifactor authentication in the external Identity provider, as this will not automatically be triggered. Example: https://docs.microsoft.com/en-us/azure/active-directory/authentication/tutorial-enable-azure-mfa |
| Info |
|---|
Require multi-factor authentication is now supported on Identity providers with OIDC. Contact support if you need MFA support enforcing on Identity providers with SAML. |
...