This guide takes you through the steps of setting up Okta login to the following Atlassian applications:
Jira
Status colour Blue title SERVER Status colour Blue title DATA CENTER Confluence
Status colour Blue title SERVER Status colour Blue title DATA CENTER Bitbucket
Status colour Blue title SERVER Status colour Blue title DATA CENTER Bamboo
Status colour Blue title SERVER Fisheye / Crucible
Status colour Blue title SERVER
| Expand | ||
|---|---|---|
| ||
You find a link to Atlassian Marketplace in the upper right corner of your Atlassian application. Click Manage apps and search for “Kantega”. Click “Free trial” or “Buy now” to install the app. |
Add identity provider
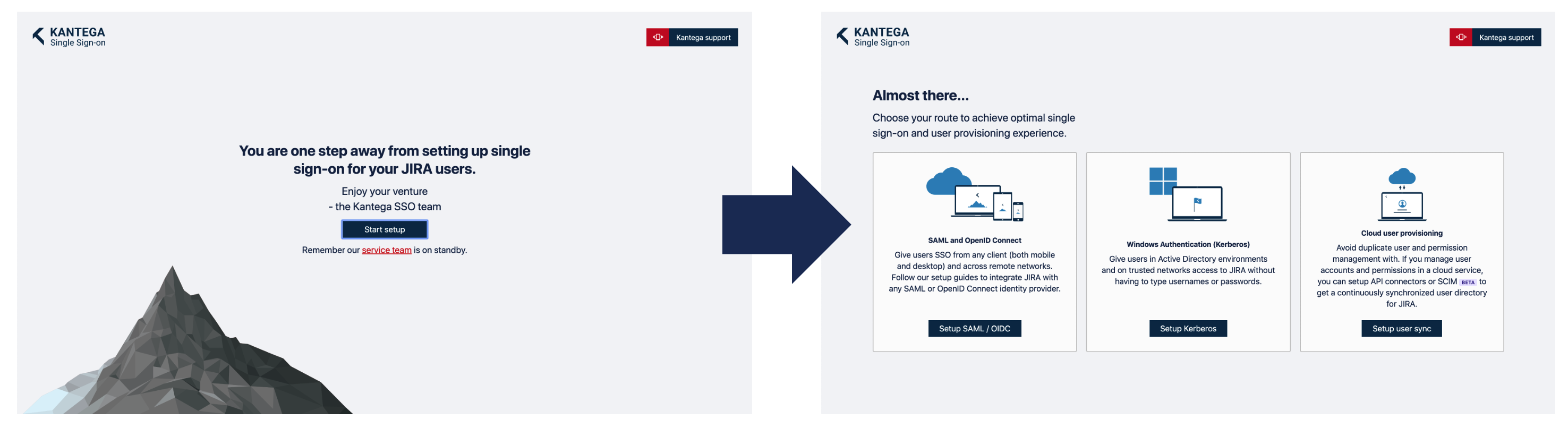
A welcome message is shown when you select to configure the app for the very first time. Click “Start setup” and then “Setup SAML / OIDC”.
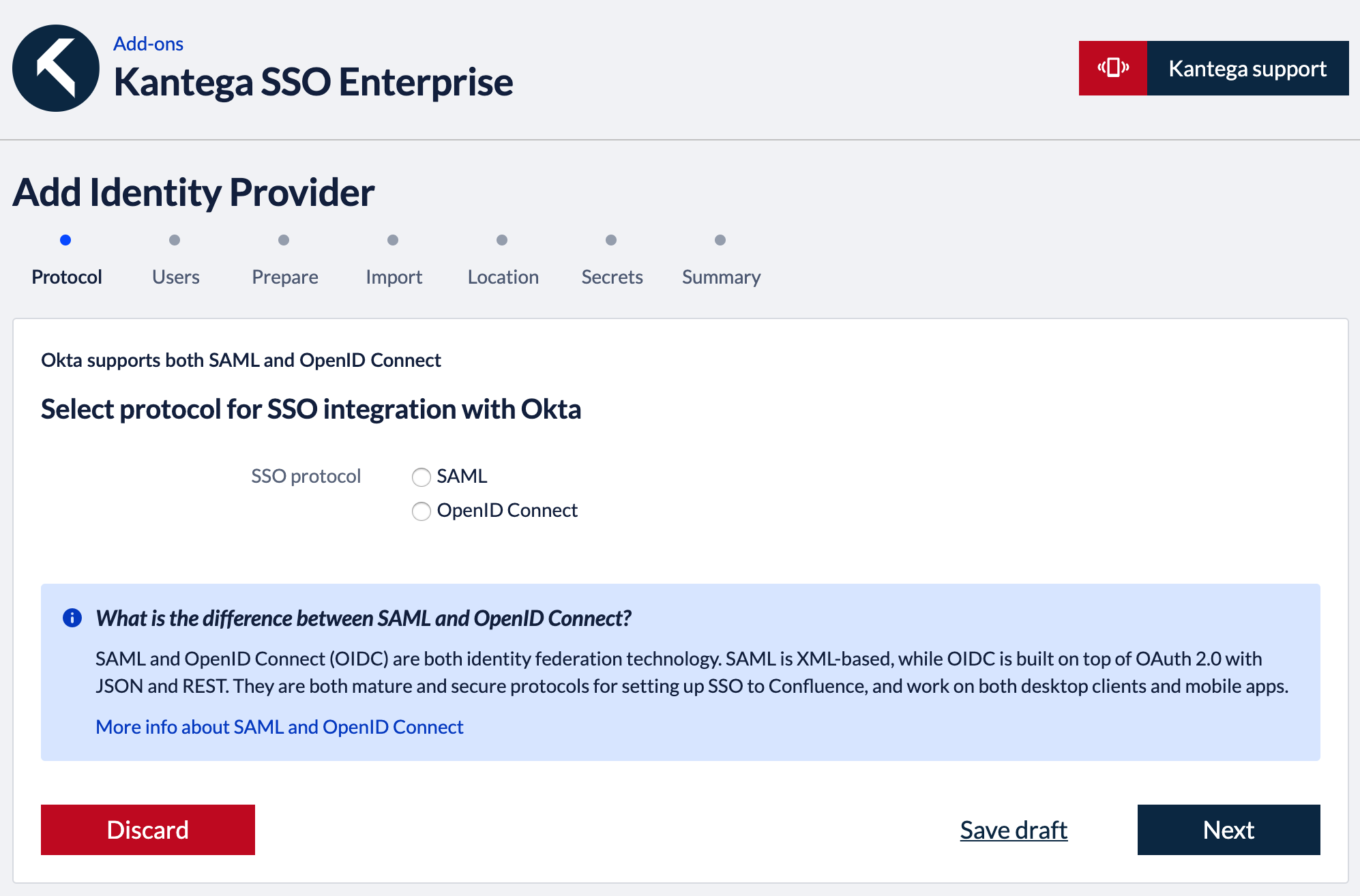
Select “Okta” in the identity provider gallery.
Okta allow you to setup single sign-on over both SAML and the OpenID Connect protocol. This knowledge base article describe the practical differences of these two protocols.
In the first wizard step, you select which SSO protocol to use. Click “Next”. Follow the protocol specific setup guides below.
| Expand | |||||
|---|---|---|---|---|---|
| |||||
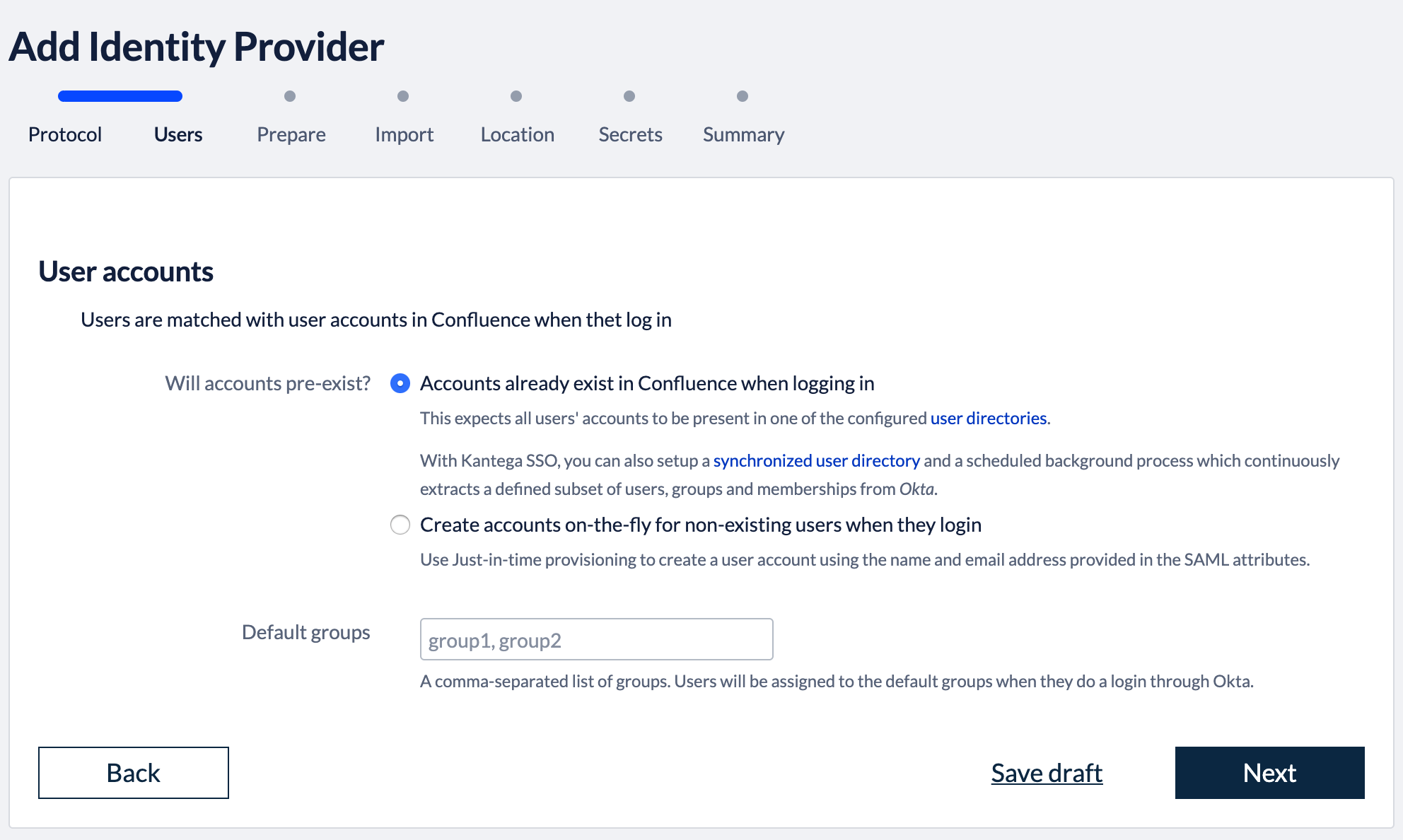
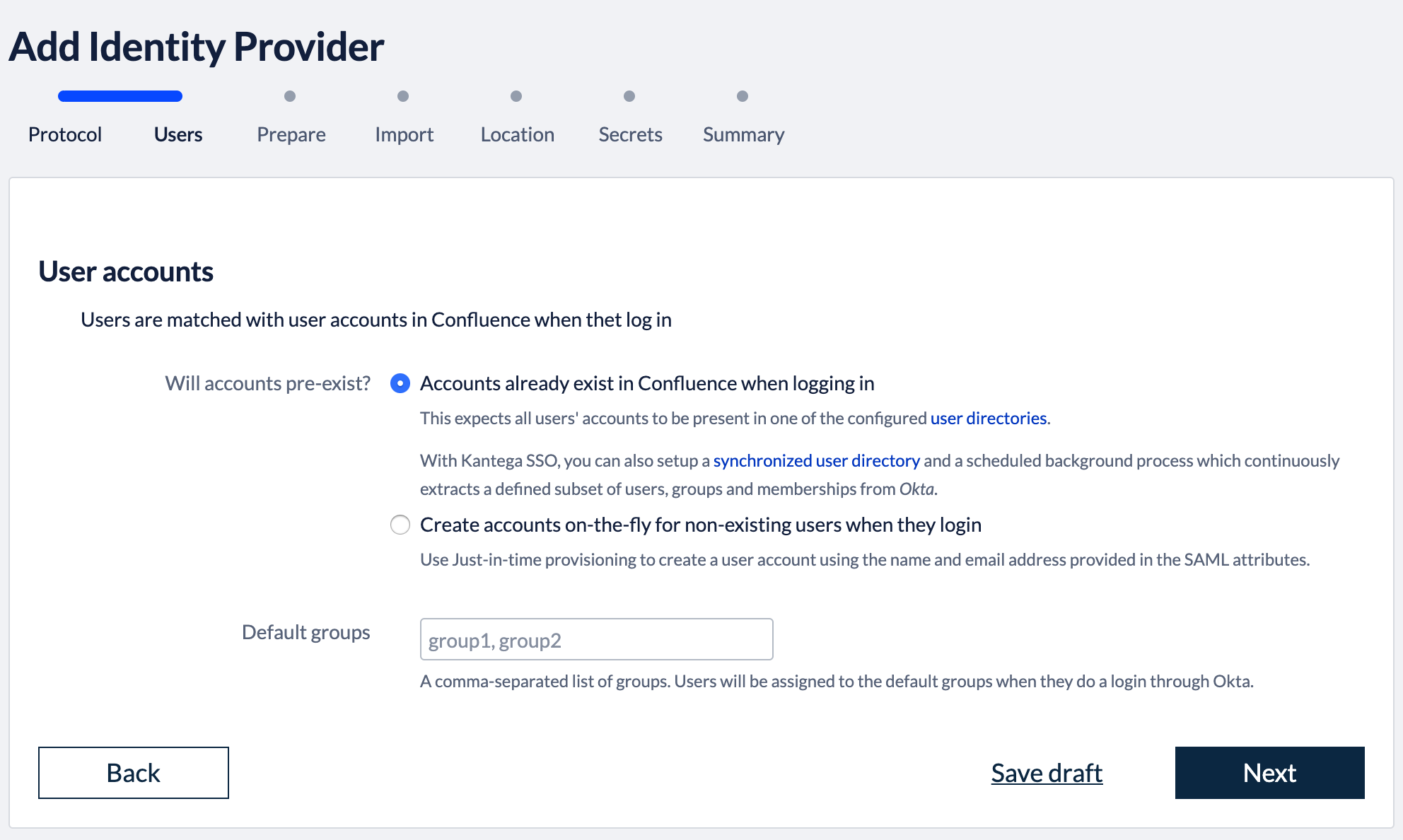
1. Select provisioning methodThe Atlassian applications needs to have information about users logging in and their permissions. At this wizard step, we choose whether user and permission data already exist when users log in with SSO or if user records should be created dynamically (just-in-time provisioning). Note that, Kantega SSO Enterprise does also offer cloud user provision provisioning with API Connectors for Okta. This will give you a user directory that reads out user and permission data from Okta and is always kept up-to-date and synchronized. More information about user provisioning alternatives are found here
You can also specify whether users logging in through Okta should be added as members to a set of default groups automatically. Alternatively, you can also retrieve and assign group memberships individually based on attributes in the SAML response. Such configurations are available after the initial setup. Select provisioning method, default groups and click “Next”. 2. Configure identity providerGo to https://admin.google.com Select Apps in the main menu Select SAML apps in the apps settings.
Press the round "+" button to add a new SAML app:
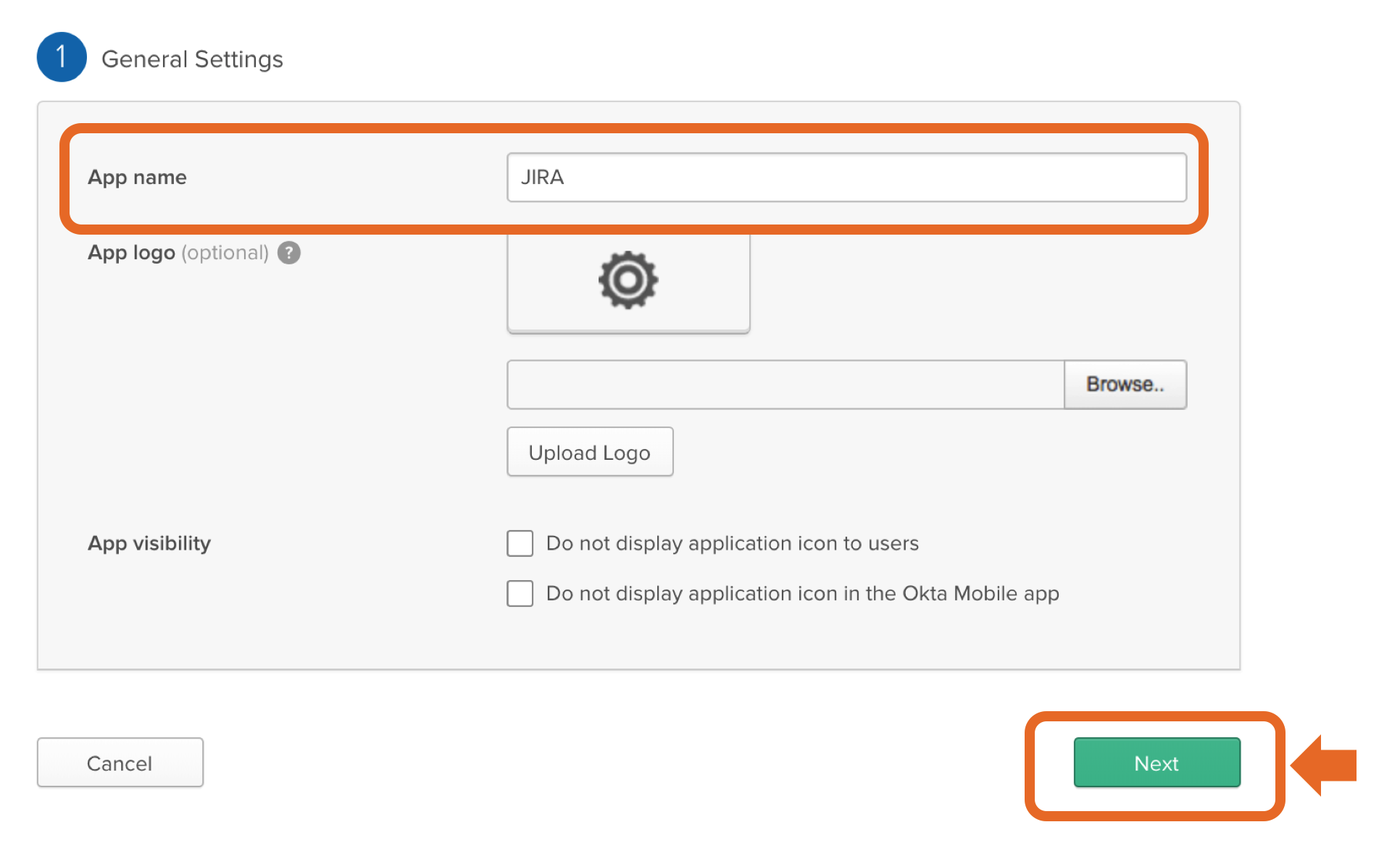
Enable SSO for SAML Application: Press "Select my own custom app" link of the dialog window: Google IdP Information:On this step only click to download Google's IDP metadata. You will upload this metadata file in the next step of this setup wizard. Basic Information for your Custom App Use a descriptive name for your app, such as "JIRA". Then press “NEXT”.
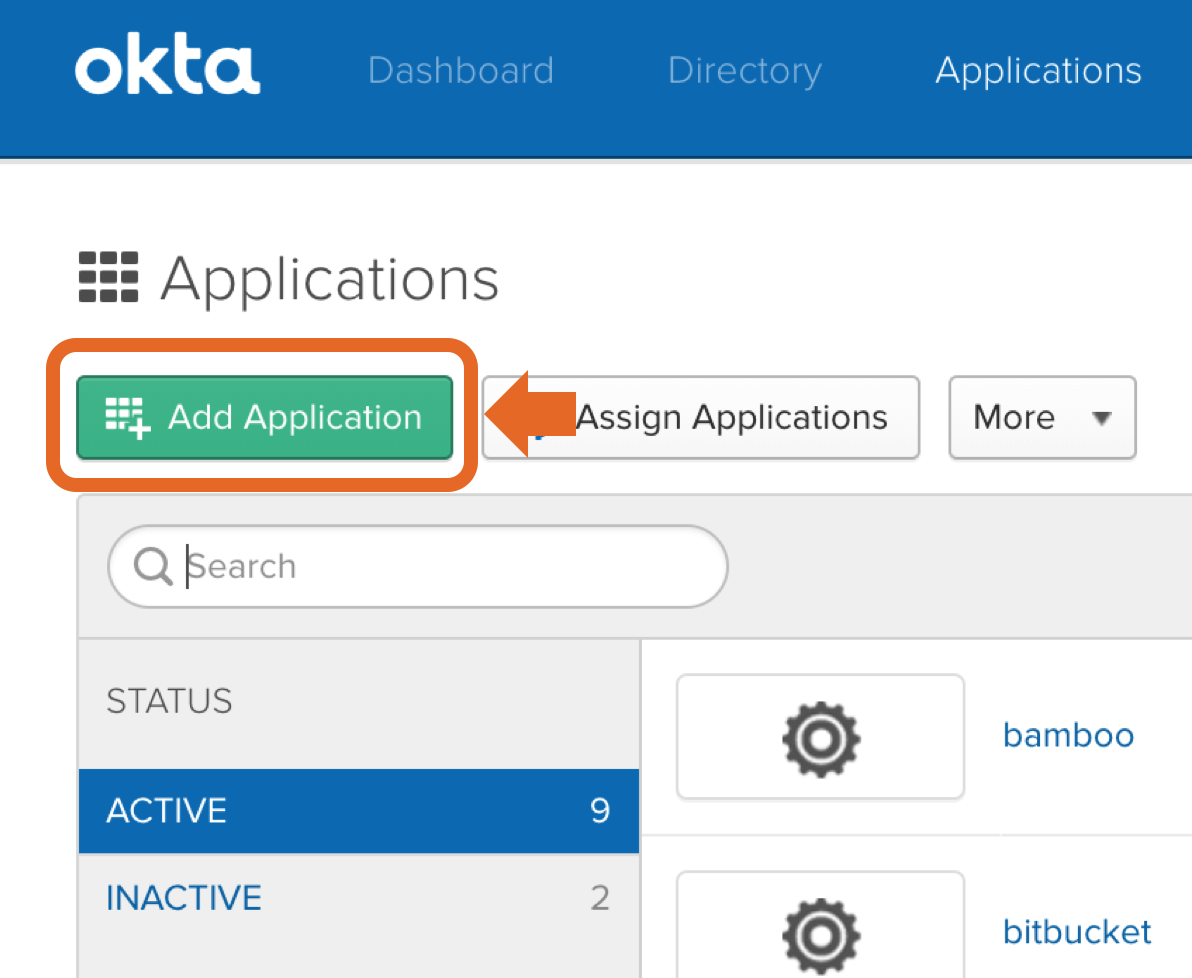
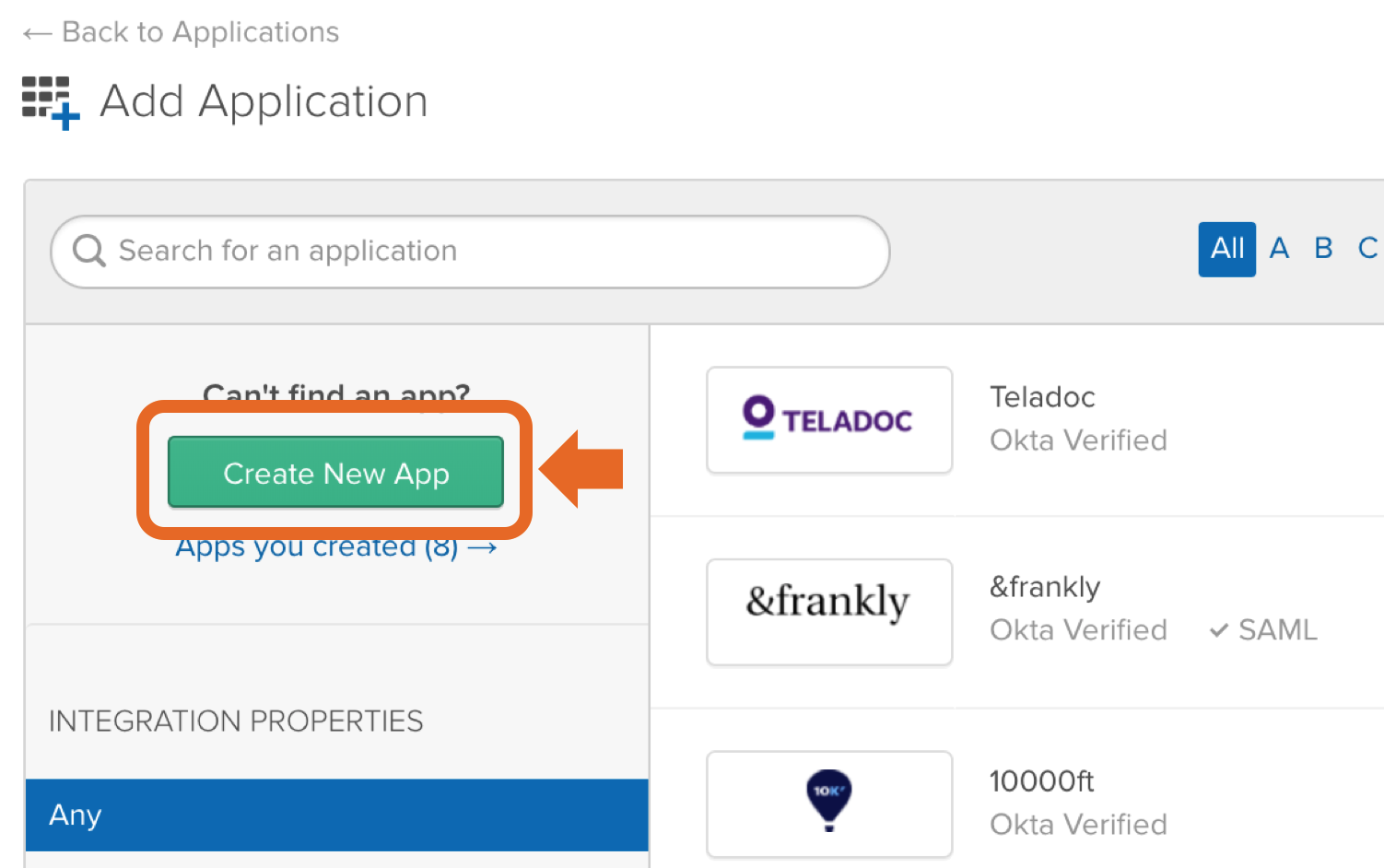
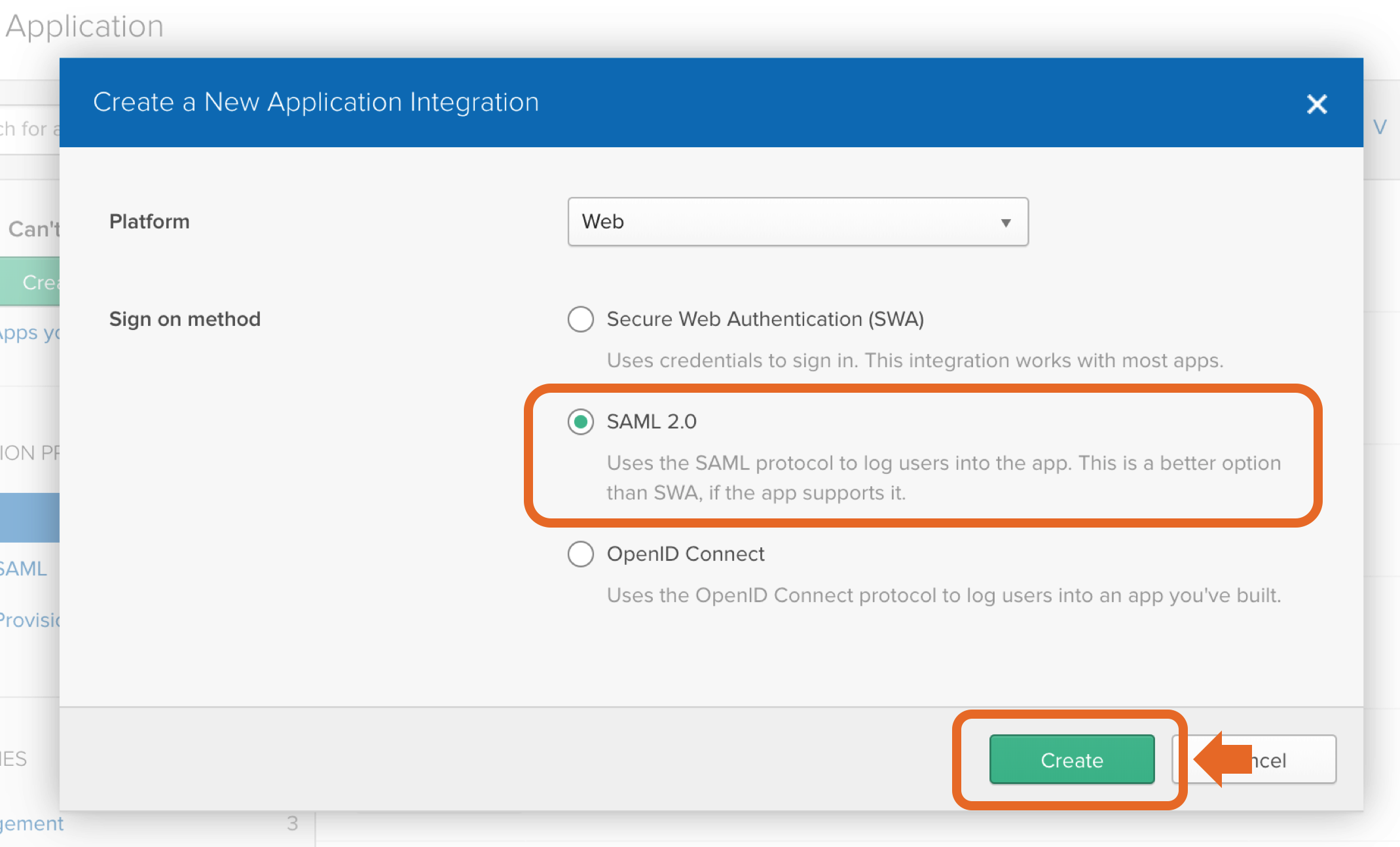
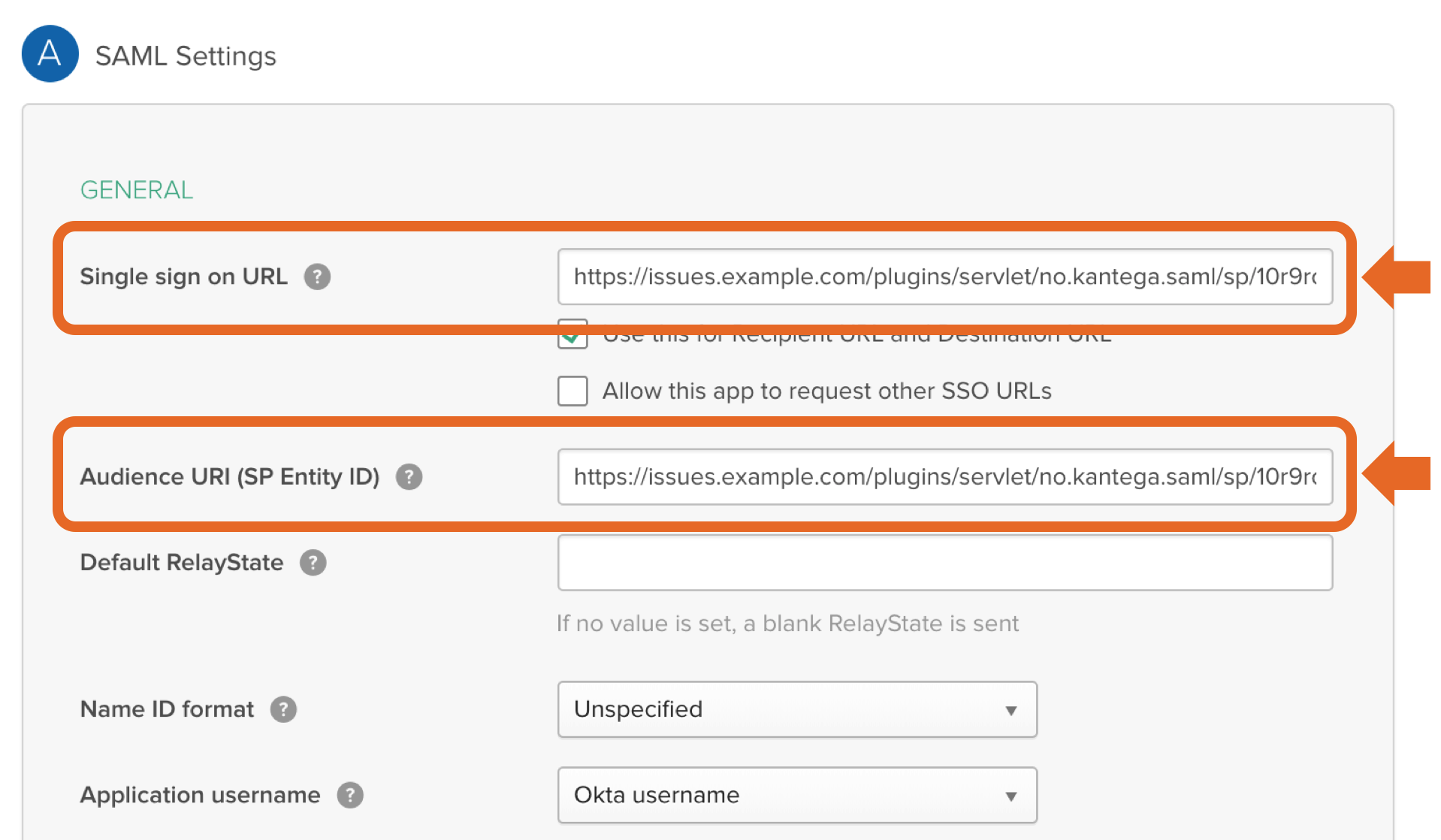
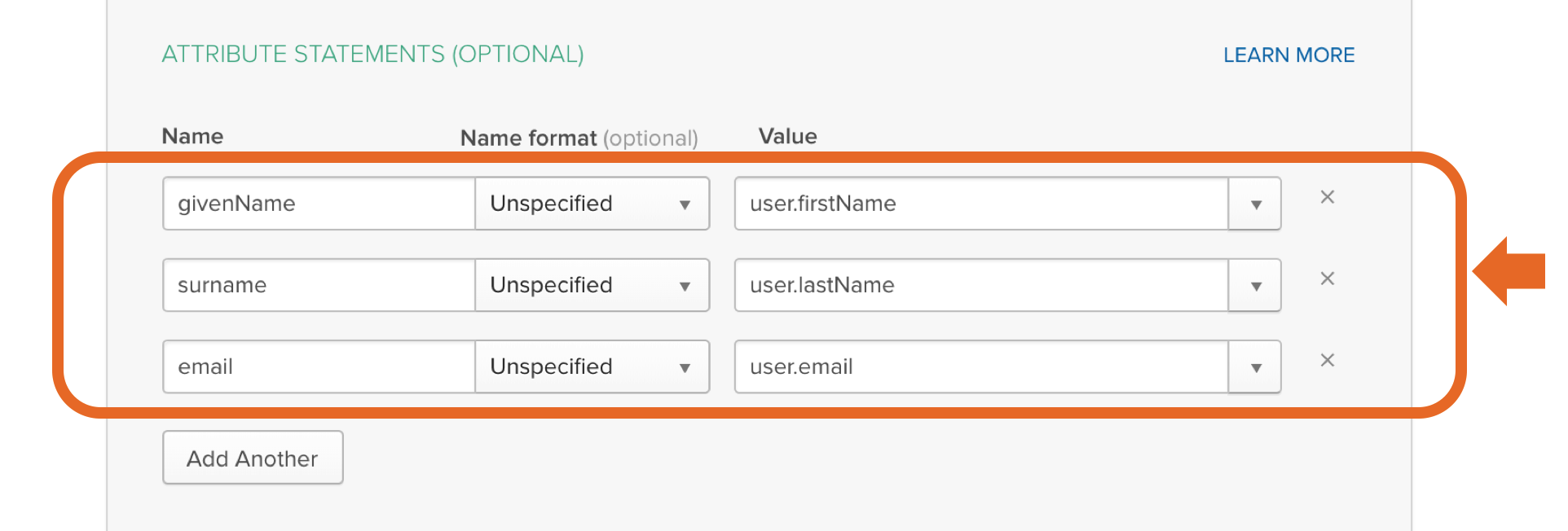
Service Provider Details Login to Okta as an admin user. Click the "Admin" button in the header. Click “Developer Console” up to the right and select “Classic UI”. Click the "Applications" link in the header. In the application page, click "Add Application". Then, click "Create New App". Choose "Web" as platform and "SAML 2.0" as sign on method. Enter an app name in General Settings. Optionally upload a logo, and click "Next". Copy the response URL from the setup wizard (back in the prepare step in the Kantega SSO wizardconfiguration) into the ACS fields "Single sign on URL and Entity ID: Leave other fields blank and press “NEXT” Attribute Mapping On this step, add the correct mapping for attributes givenName, surname and email. All of the fields should be of type "Basic Information" Enable the app for users Make sure to set the "Service status" to "ON for everyone" on your GSuite SAML app. If you want the Google login to only apply to a subset of the organization, you can choose "On for some". With this setting, users in other parts of the organization will be exposed with a "Service not enabled"-message after their username / password is given. You may now close the G Suite browser window. Click “Next” in the Kantega SSO wizard. 3. Import metadataUpload the metadata file that we downloaded from Google during the identity provider configurations (previous step). Click “Next”" and "Audience URI (SP Entry ID)". In "Attribute statements", set up the following attributes:
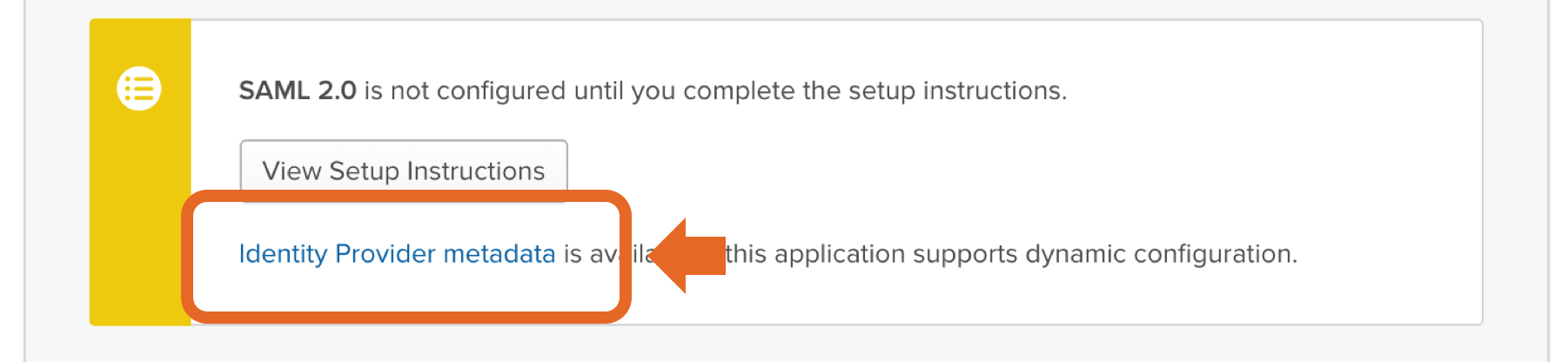
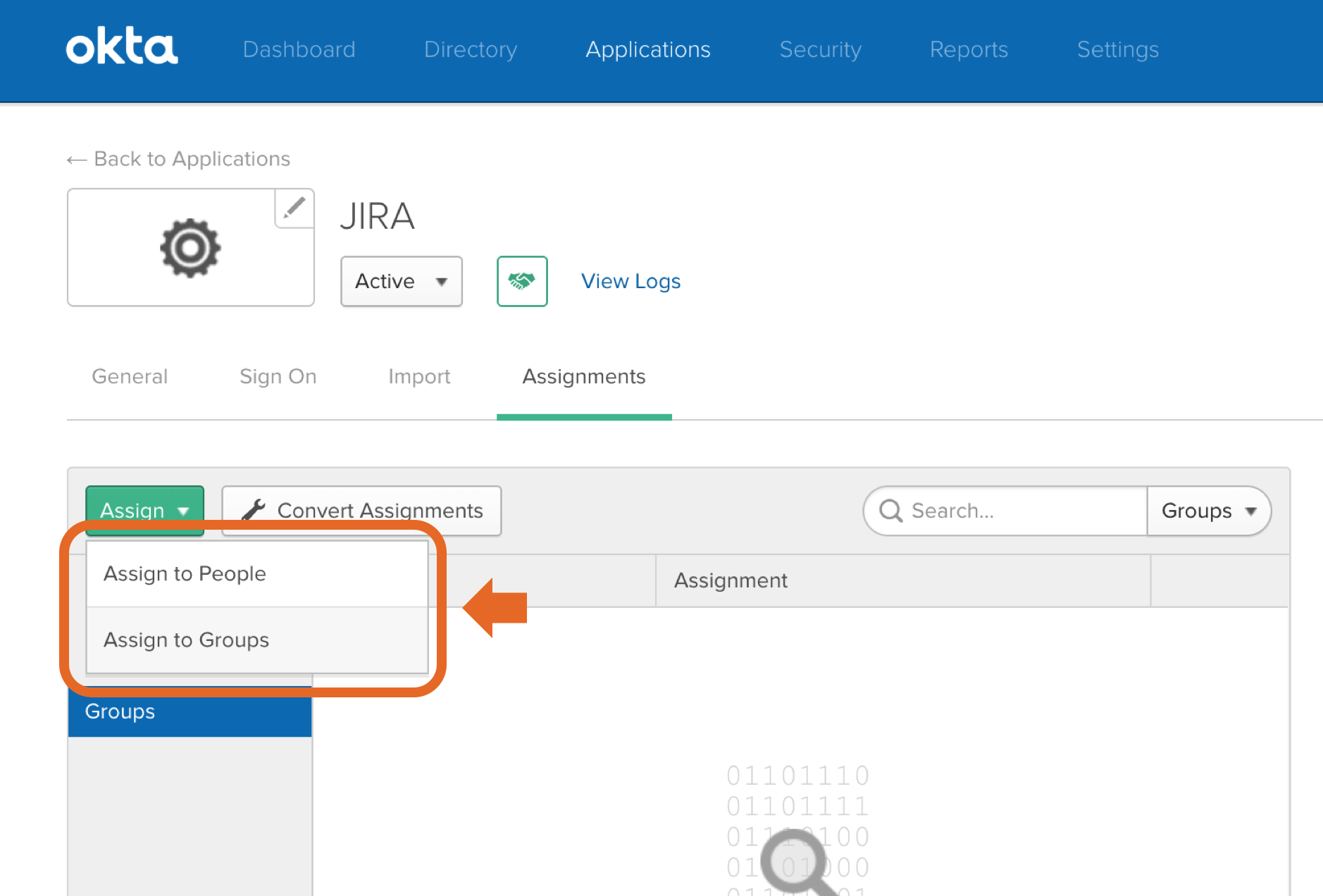
Click “Next”, then “Finish”. Right click on the "Identity Provider metadata" link (see illustration above) and copy the URL to your clipboard. You will need this link in the next step of this wizard. Assign People and/or Groups to your appNow Okta users needs be assigned to (which means to get access to) your application. Click the "Assignments" tab. Further, when you click the green "Assign" button, you can choose to assign users individually or through their group memberships. To assign a group to your application:
To assign people individually:
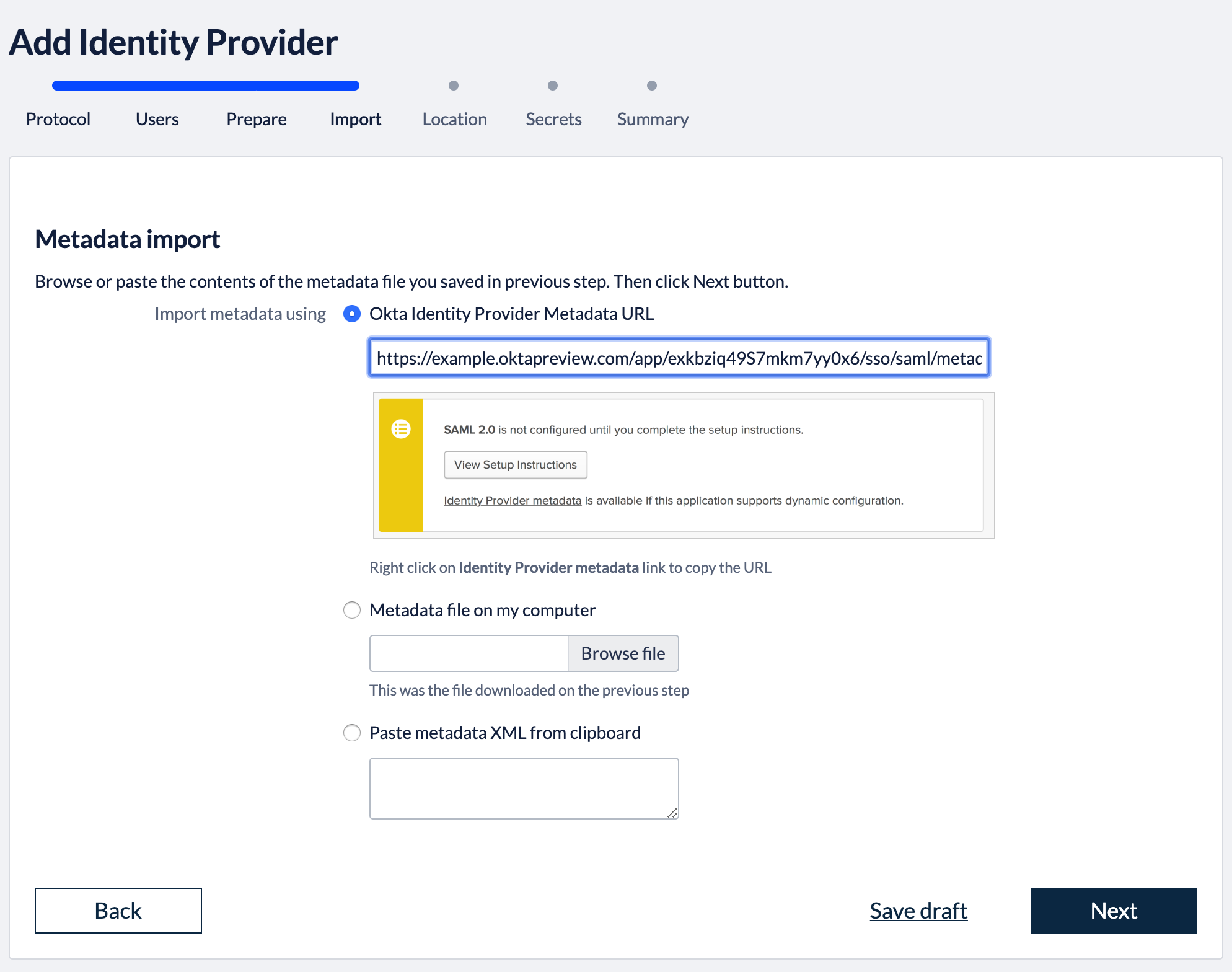
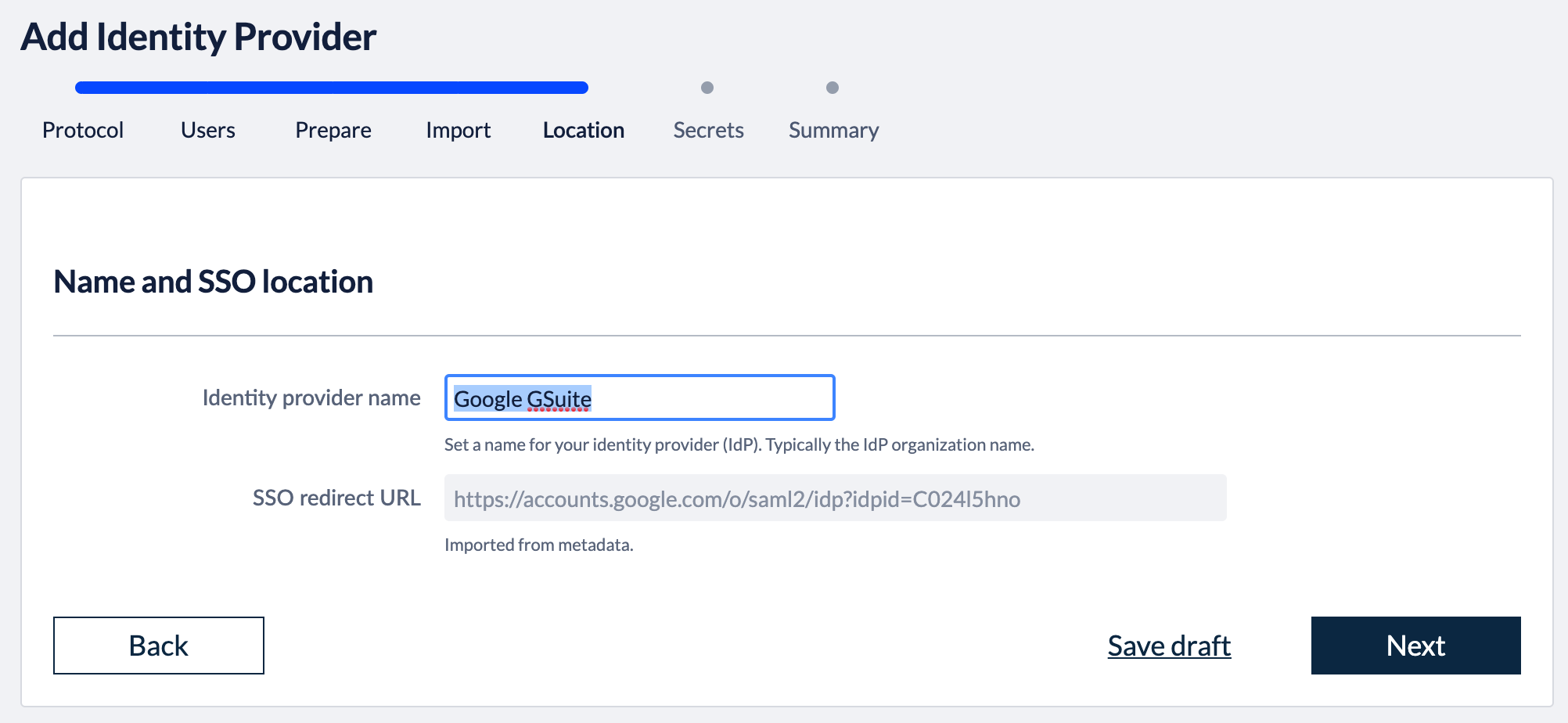
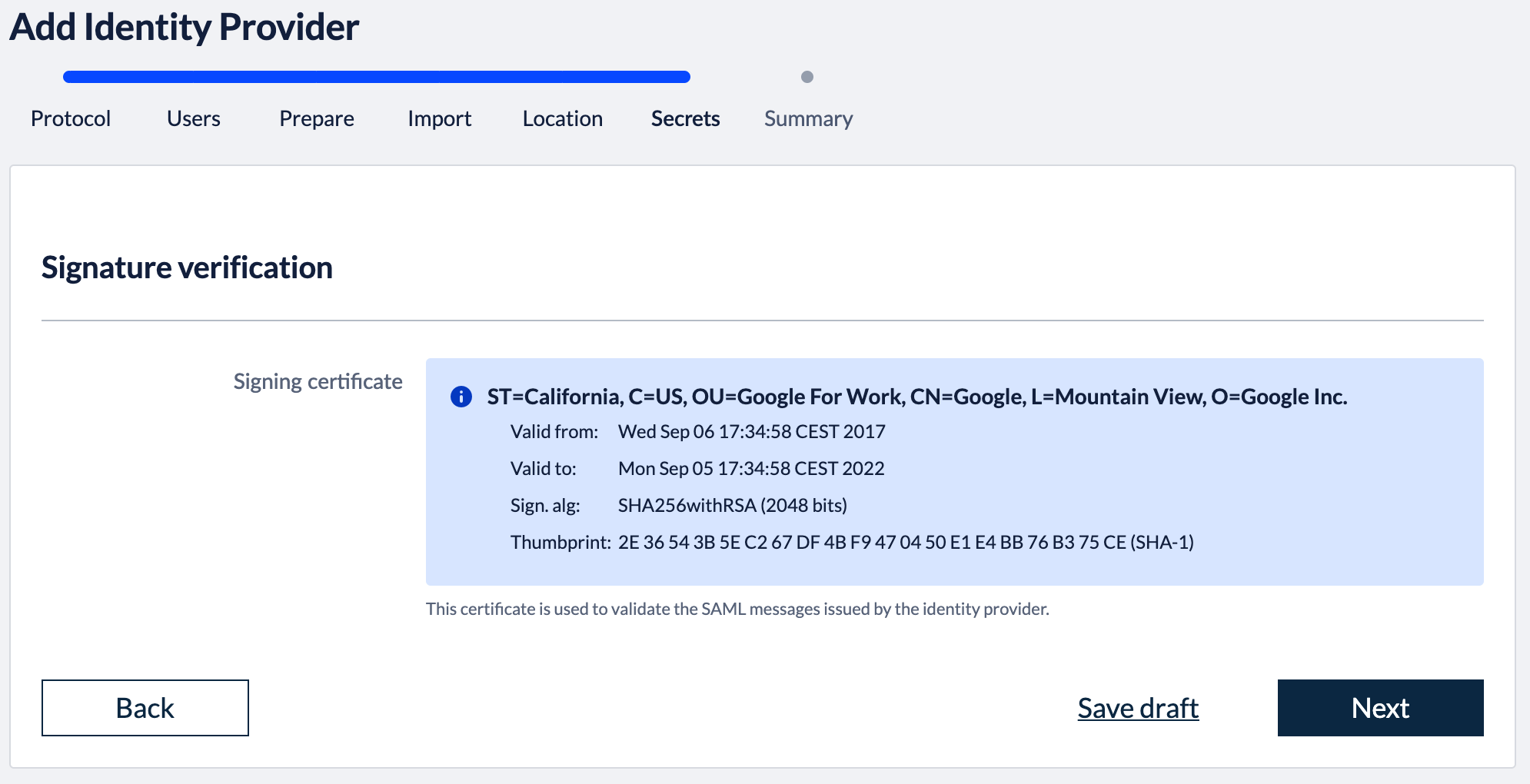
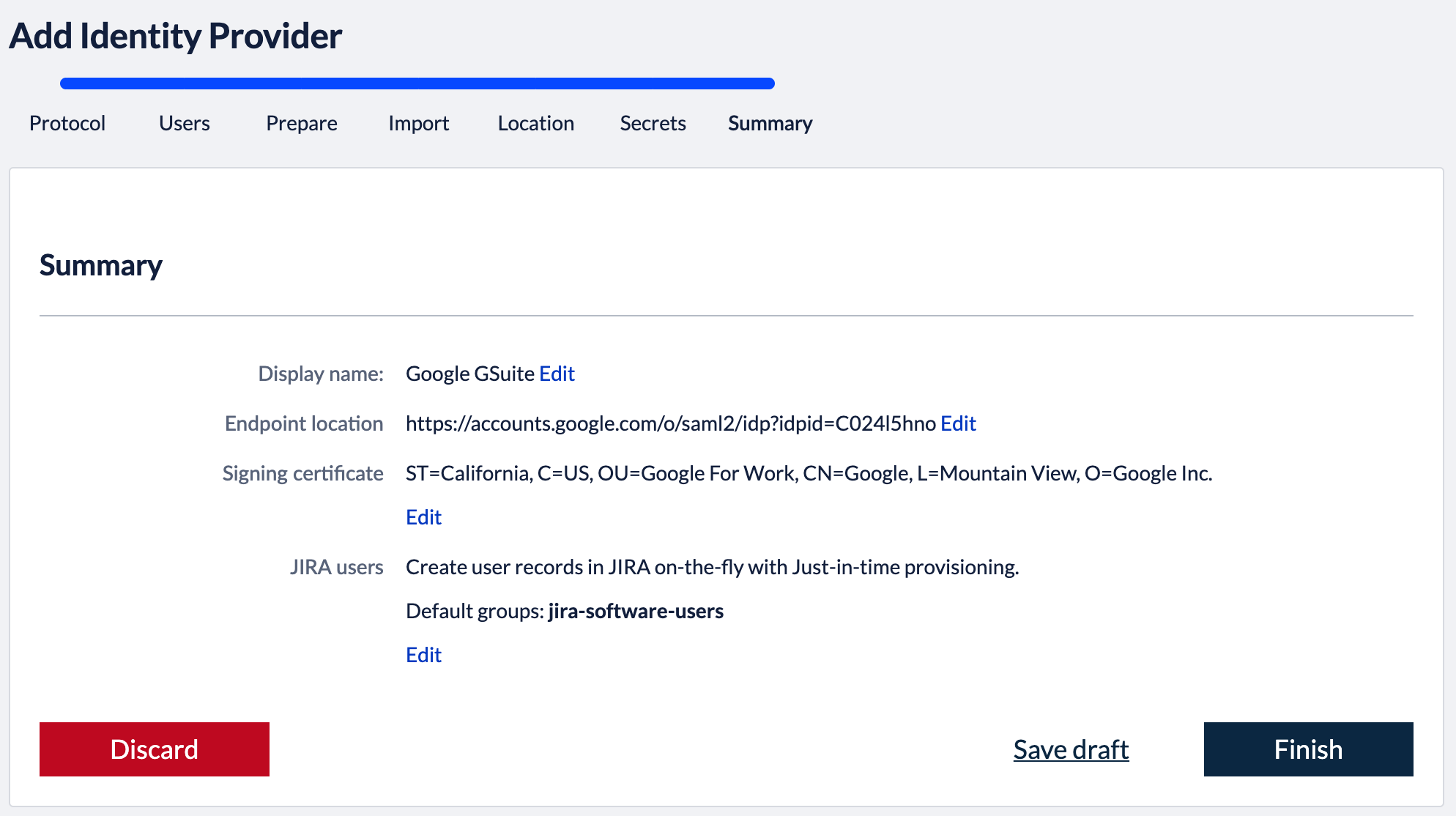
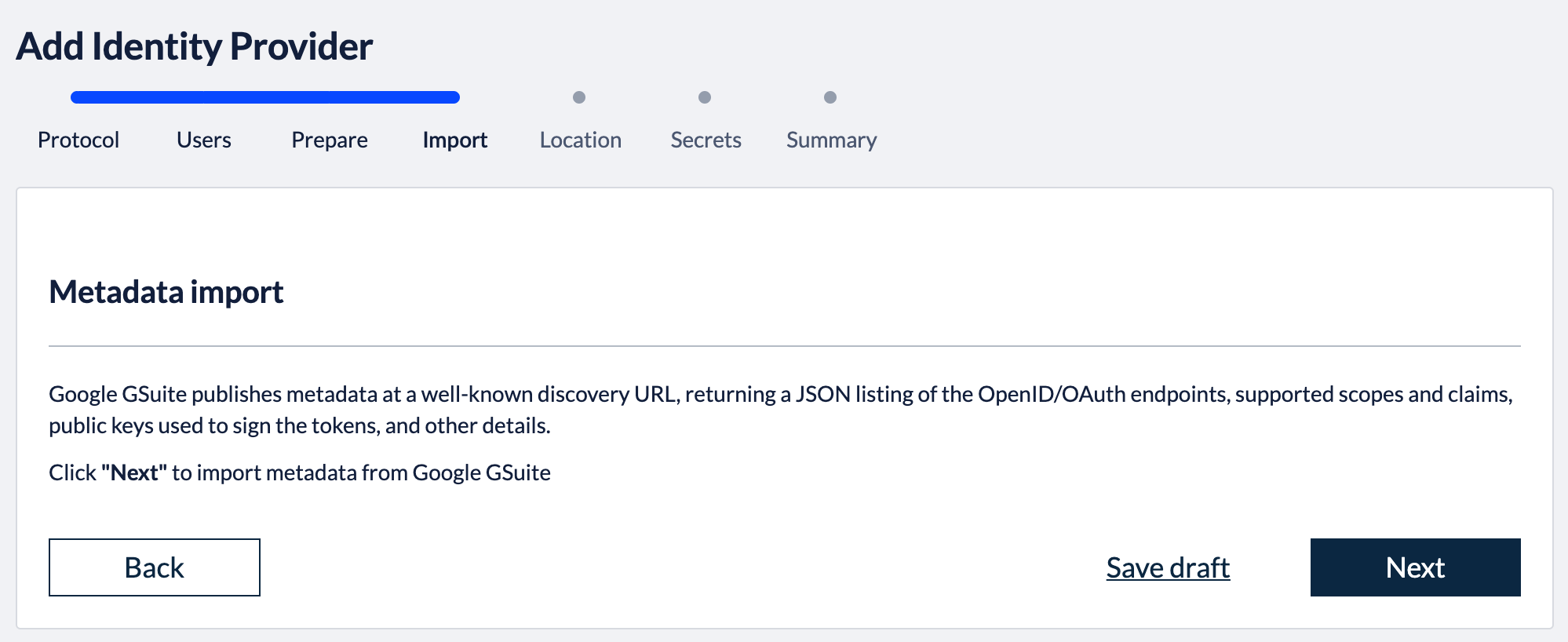
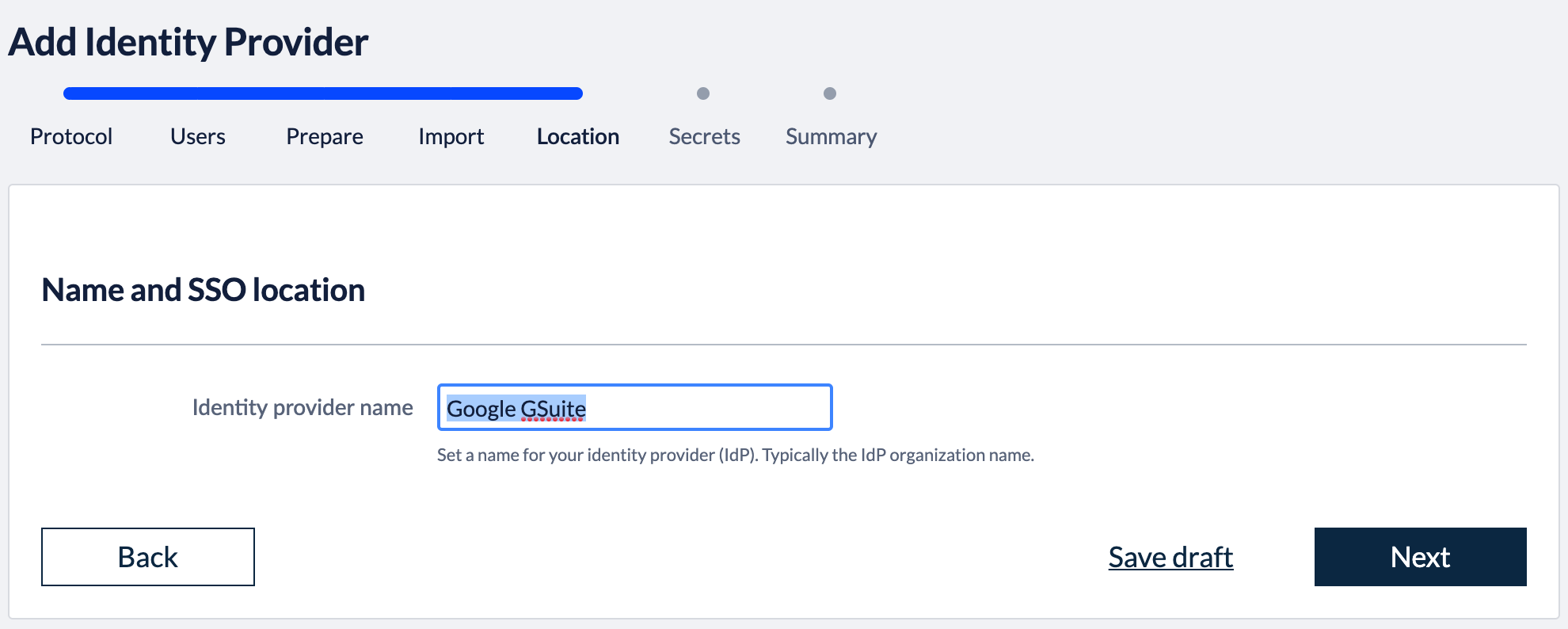
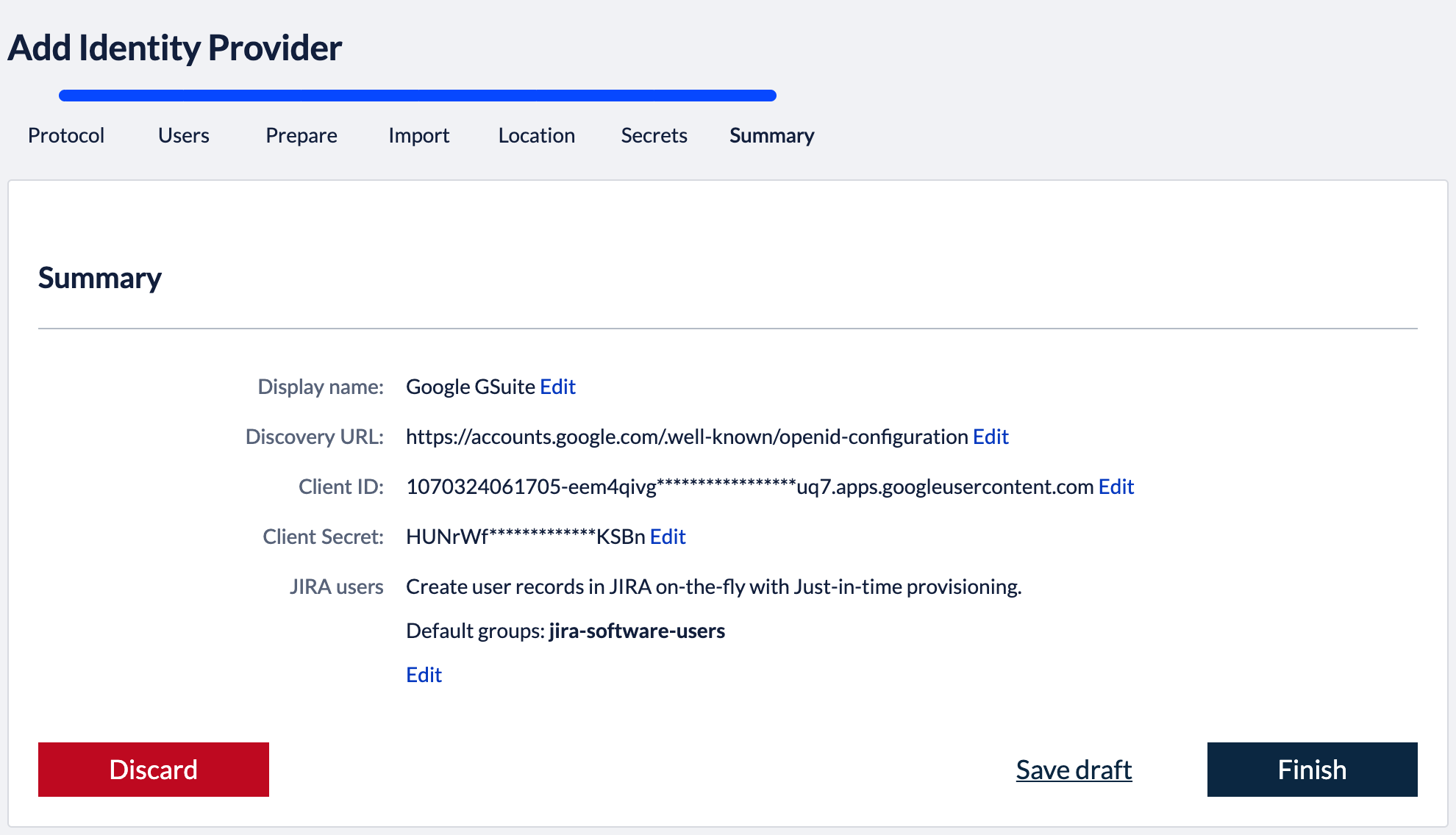
3. Import metadataBack in the Kantega SSO setup wizard you can now press "Next" to get to the import step. Paste in the metadata url (See instructions above regarding copying metadata url from Okta). Click “Next”. 4. Identity provider nameFill in a name for your configuration, by default this is “Google GSuite”. Click “Next” 5. Verify signatureThis step shows the certificate used to validate the SAML messages. Click “Next”. 7. SummaryValidate your setup and click “Finish”.
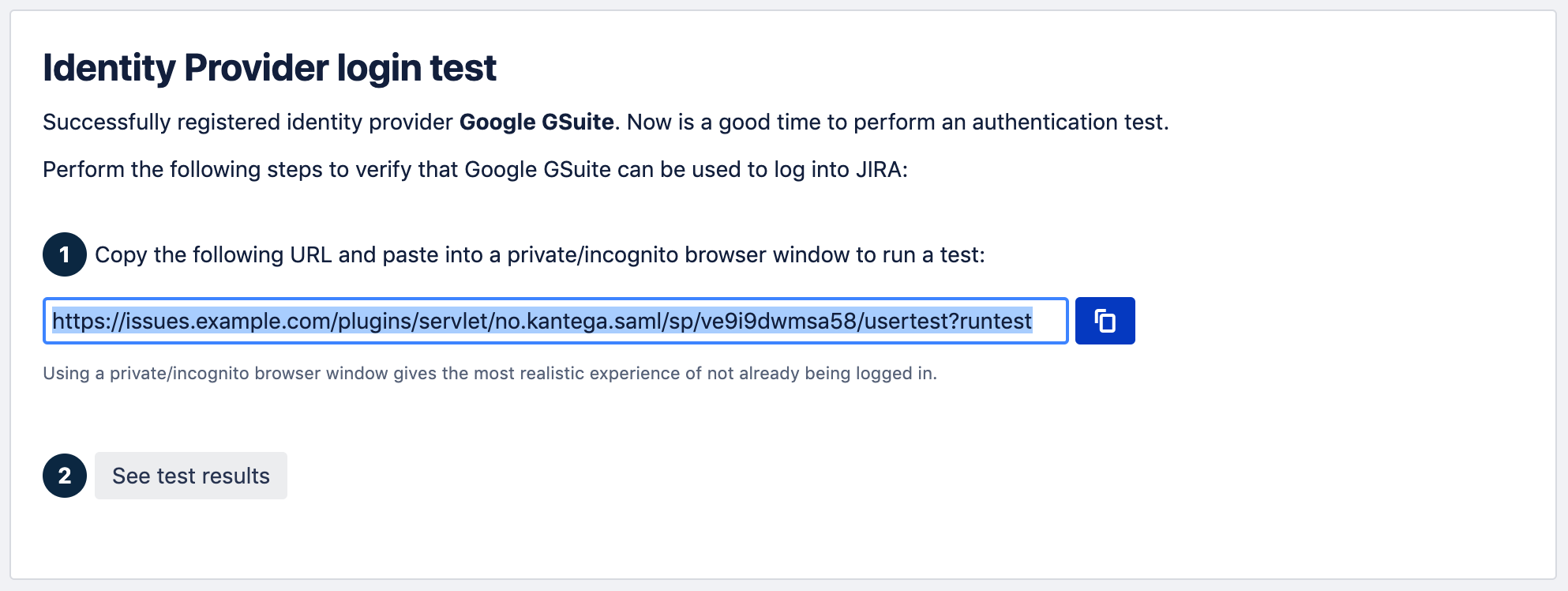
8. Test and verify setupOn the next page you will be given a link to perform a test of your setup. The test verifies that users are allowed to authenticate with the current configuration, and you get feedback on whether the current user is found in Atlassian application. You are also able to fix user lookup issues (selecting the right username attribute and express username transformation rules) and select data attributes for just-in-time provisioning here. More info about testing av verifying identity provider configurations. 6. Redirection modeBy default, Kantega SSO Enterprise will forward all users to the configured identity provider. However, you can configure both a subset of users who should be login through this identity provider and how they are redirected. More about configuration redirection rules. |
| Expand | |||||
|---|---|---|---|---|---|
| |||||
1. Select provisioning methodThe Atlassian applications needs to have information about users logging in and their permissions. At this wizard step, we choose whether user and permission data already exist when users log in with SSO or if user records should be created dynamically (just-in-time provisioning). Note that, Kantega SSO Enterprise does also offer cloud user provision provisioning with API Connectors for Okta. This will give you a user directory that reads out user and permission data from Okta and is always kept up-to-date and synchronized. More information about user provisioning alternatives are found here
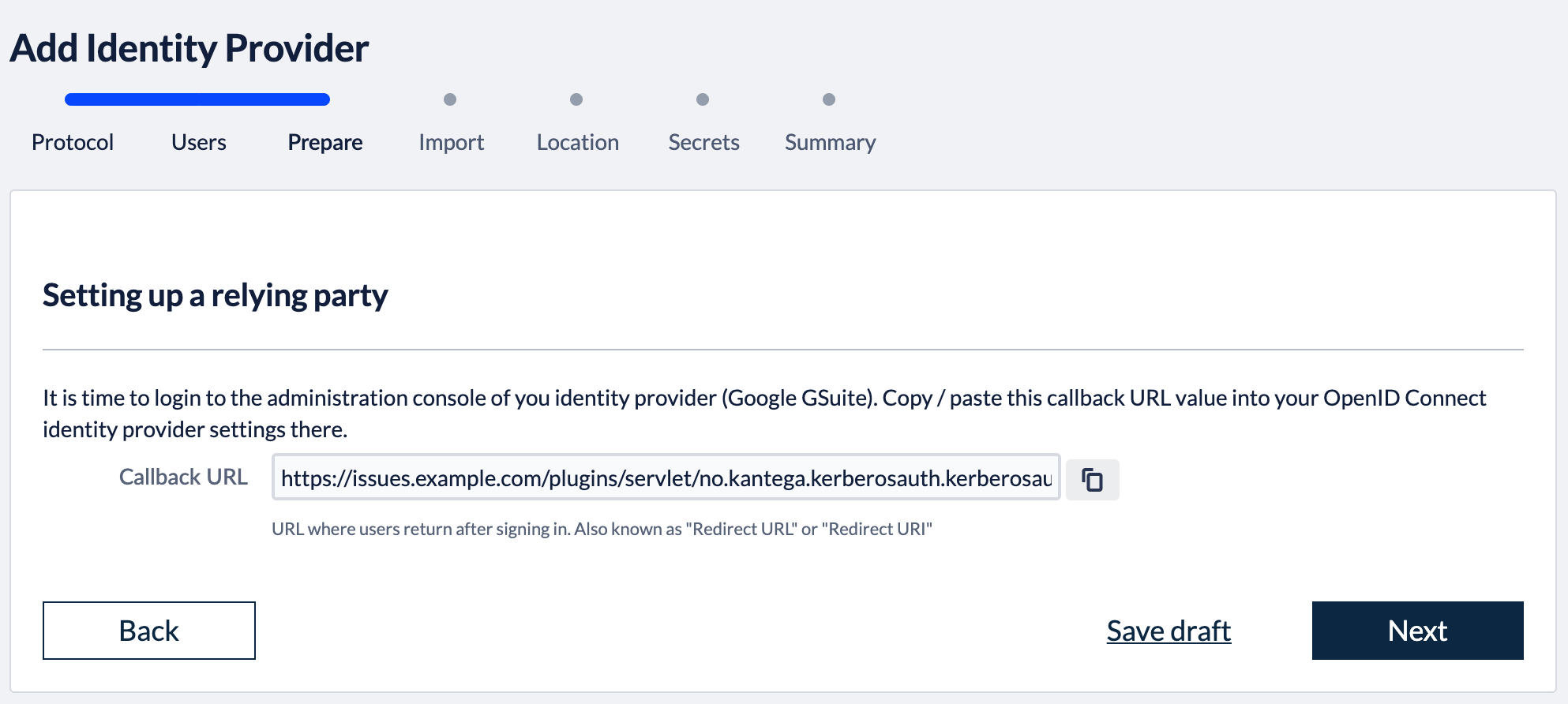
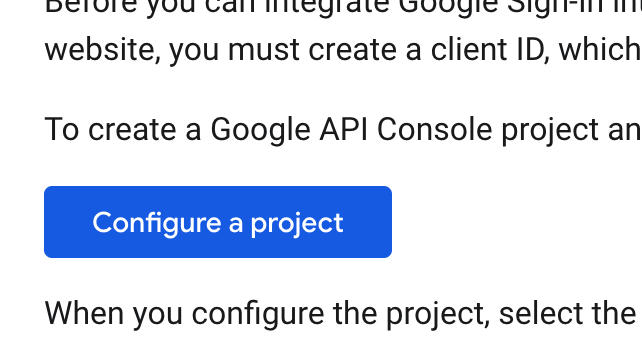
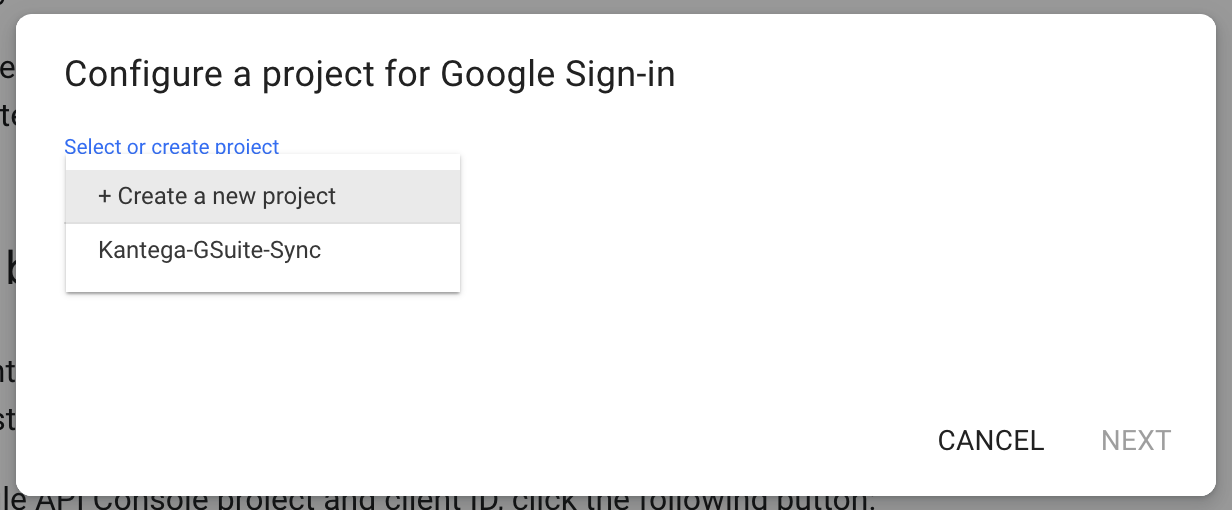
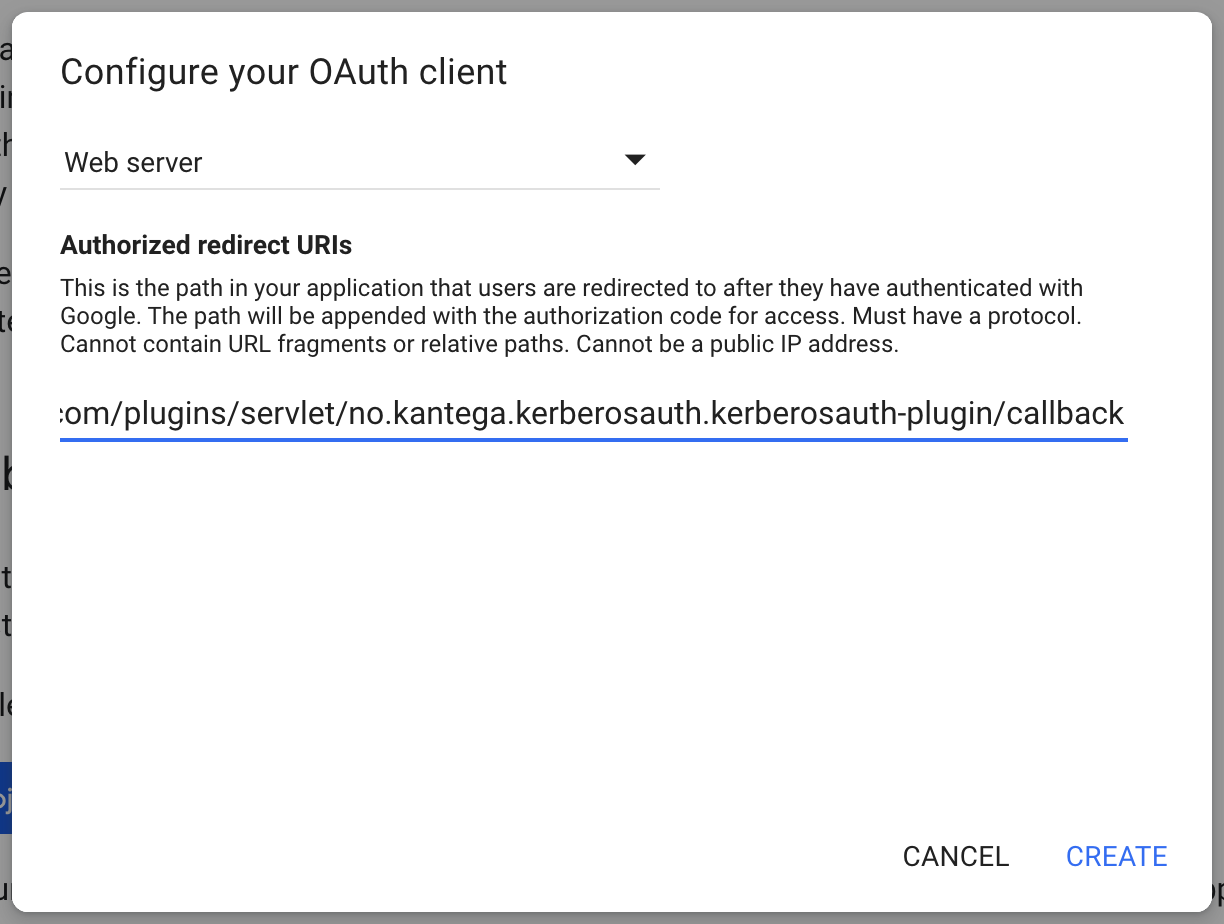
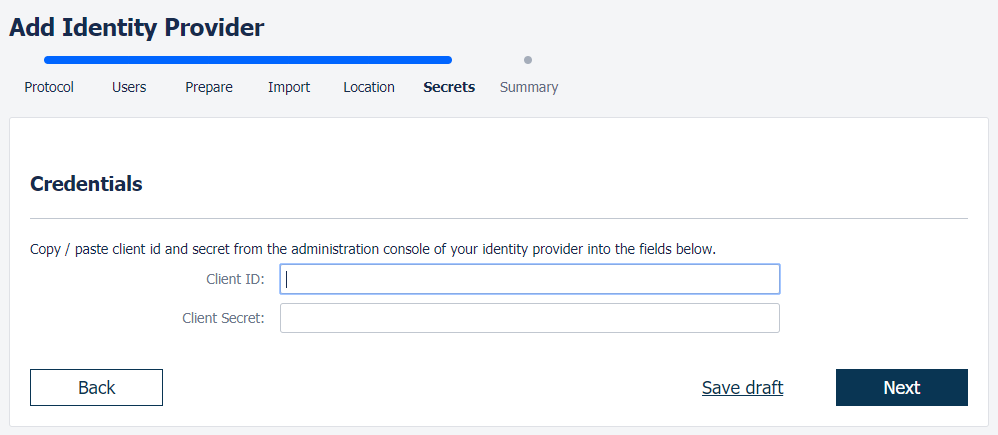
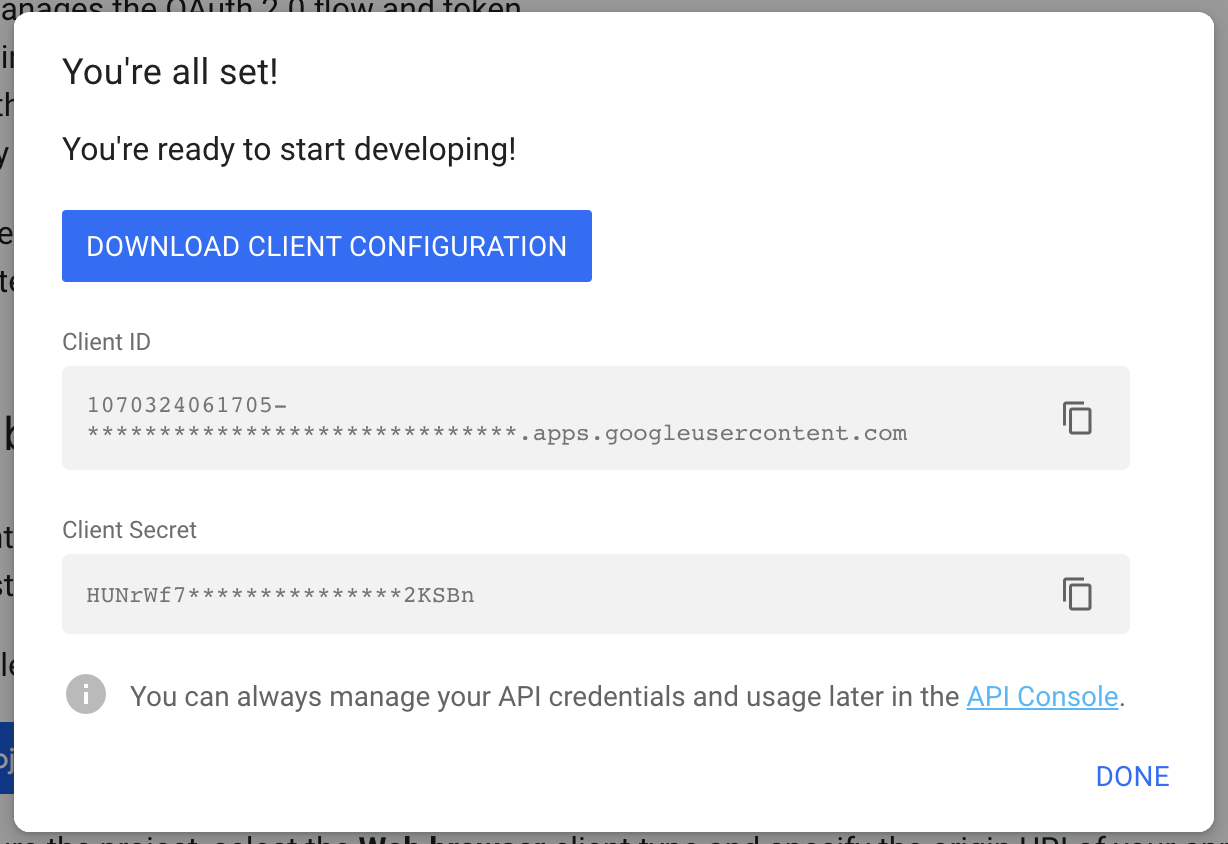
You can also specify whether users logging in through Okta should be added as members to a set of default groups automatically. Alternatively, you can also retrieve and assign group memberships individually based on attributes in the SAML response. Such configurations are available after the initial setup. Select provisioning method, default groups and click “Next”. 2. Callback URLThe field “Callback URL” will be needed when configuring your identity provider. Copy this URL value (We will make use of this in the next step) 3. Configure identity providerSign in to https://developers.google.com/identity/sign-in/web/sign-in Click the blue “Configure a project”-button Select an existing project or create a new. Then click “NEXT”. Select “Web server” in the “Where are you calling from?” dropdown list, and insert the callback-url (which we copied from the Kantega SSO setup above) into the text input field. Click “NEXT”. 4. Import metadataGo to the Kantega SSO wizard and click “Next” in the import step 5. Identity provider nameFill in a name for your configuration, by default this is “Google GSuite”. Click “Next” 6. Client id and secretIn this step, we will insert client credentials from Google Gsuite. These two values are found here: Click “Next”, and you will see a summary page of your Kantega SSO setup. 7. SummaryValidate your setup and click “Finish”. 8. Test and verify setupOn the next page you will be given a link to perform a test of your setup. The test verifies that users are allowed to authenticate with the current configuration, and you get feedback on whether the current user is found in Atlassian application. You are also able to fix user lookup issues (selecting the right username attribute and express username transformation rules) and select data attributes for just-in-time provisioning here. More info about testing av verifying identity provider configurations. 6. Redirection modeBy default, Kantega SSO Enterprise will forward all users to the configured identity provider. However, you can configure both a subset of users who should be login through this identity provider and how they are redirected. More about configuration redirection rules. |
.gif?version=1&modificationDate=1584470017790&cacheVersion=1&api=v2)