With Just-in-Time (JIT) provisioning, you can use SAML assertions or OpenID Connect user info endpoints to create and update Atlassian users accounts on the fly when they log in. This eliminates the need to create user accounts in advance. For example, if you recently added an employee to your organization, you don't need to manually create the user in Atlassian application. When they log in with single sign-on, their account is automatically created for them, eliminating the time and effort with on-boarding the account. Just-in-Time provisioning works with any writable user directory (Internal directories, Delegated LDAP, and Atlassian Crowd).
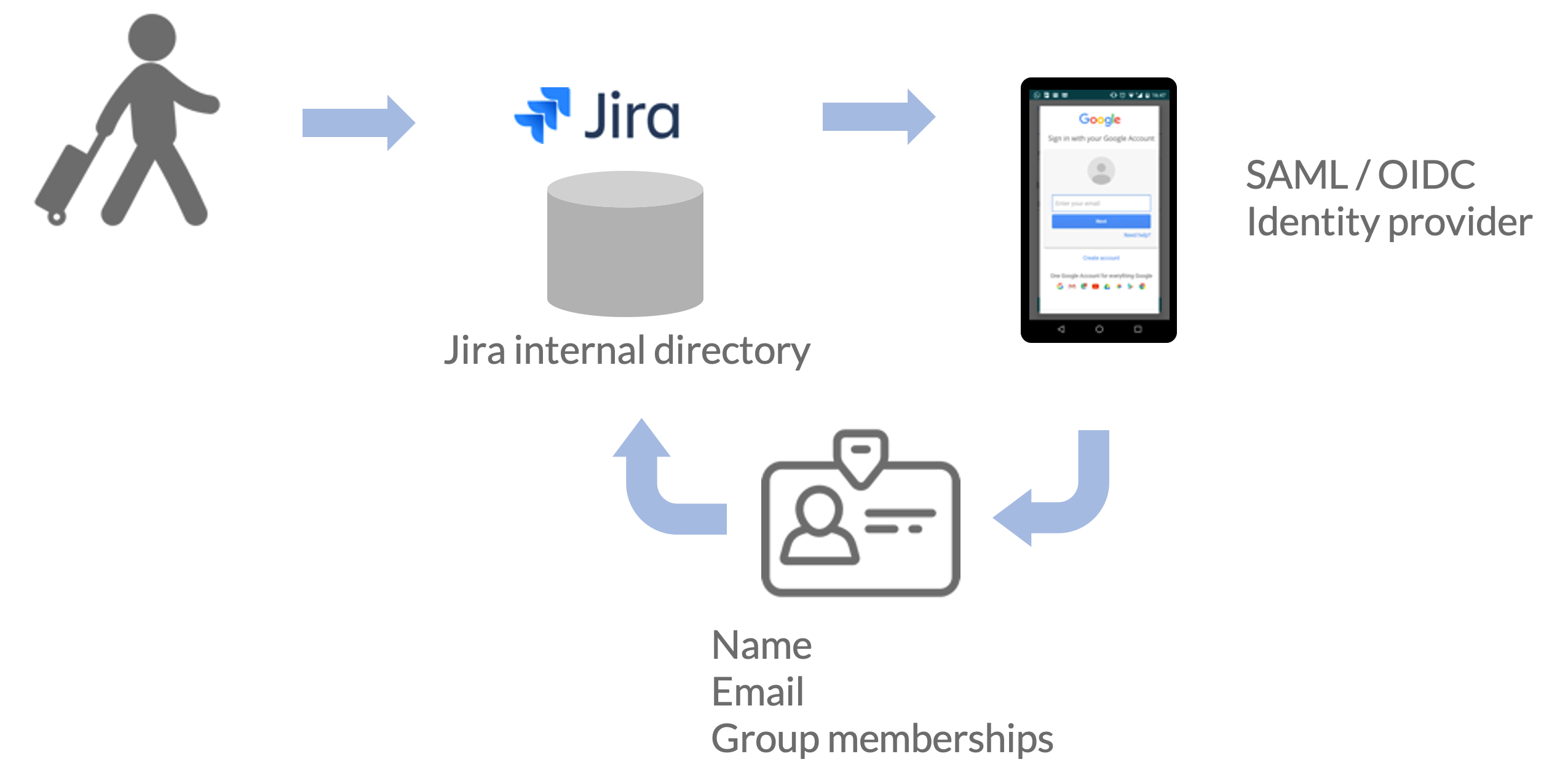
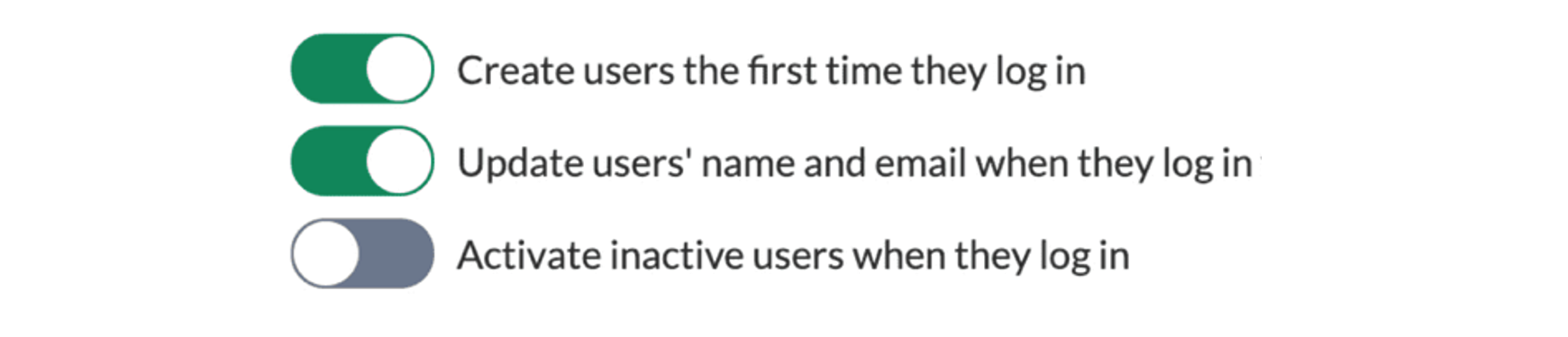
Admins can specify whether users should be created, updated and activated and also specify which user directory to work against in the JIT configuration page in the Kantega SSO Enterprise app.
Group memberships can be applied during SAML and OpenID Connect login, and as an admin you can both specify default-, auto created and managed groups.
Default groups are a static set of groups that all users will be assigned to when they log in through a specific identity provider.
Auto created groups when enabled will create all groups and assign users to all claims included by the identity provider in the SAML response or OIDC token. You may also remove memberships from user that does not exist in the incoming claim. In this way all group memberships that your identity provider has for a given user will be synchronized on each login.
Managed groups, on the other hand, uses membership claims included by the identity provider in the SAML response or OIDC token and synchronizes only the groups you have specifically configured.